Query Time: 1.29 ms Query memory: 0.023 MB Memory before query: 4.173 MB Rows returned: 0
SELECT `data`
FROM `l6r3h_session`
WHERE `session_id` = X'3531646263363430353462366364323665313164303937653831326134343834'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_session | NULL | const | PRIMARY | PRIMARY | 194 | const | 1 | 100.00 | NULL |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/libraries/joomla/session/storage/database.php:45 |
| 14 | JSessionStorageDatabase->read() | Same as call in the line below. |
| 13 | session_start() | JROOT/libraries/joomla/session/handler/native.php:260 |
| 12 | JSessionHandlerNative->doSessionStart() | JROOT/libraries/joomla/session/handler/native.php:50 |
| 11 | JSessionHandlerNative->start() | JROOT/libraries/joomla/session/handler/joomla.php:88 |
| 10 | JSessionHandlerJoomla->start() | JROOT/libraries/src/Session/Session.php:661 |
| 9 | Joomla\CMS\Session\Session->_start() | JROOT/libraries/src/Session/Session.php:621 |
| 8 | Joomla\CMS\Session\Session->start() | JROOT/libraries/src/Session/Session.php:499 |
| 7 | Joomla\CMS\Session\Session->get() | JROOT/libraries/src/Session/Session.php:456 |
| 6 | Joomla\CMS\Session\Session->isNew() | JROOT/libraries/src/Application/CMSApplication.php:826 |
| 5 | Joomla\CMS\Application\CMSApplication->loadSession() | JROOT/libraries/src/Application/CMSApplication.php:136 |
| 4 | Joomla\CMS\Application\CMSApplication->__construct() | JROOT/libraries/src/Application/SiteApplication.php:66 |
| 3 | Joomla\CMS\Application\SiteApplication->__construct() | JROOT/libraries/src/Application/CMSApplication.php:386 |
| 2 | Joomla\CMS\Application\CMSApplication::getInstance() | JROOT/libraries/src/Factory.php:140 |
| 1 | Joomla\CMS\Factory::getApplication() | JROOT/index.php:46 |
Query Time: 1.13 ms After last query: 0.91 ms Query memory: 0.020 MB Memory before query: 4.268 MB Rows returned: 0
SELECT `session_id`
FROM `l6r3h_session`
WHERE `session_id` = X'3531646263363430353462366364323665313164303937653831326134343834'
LIMIT 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_session | NULL | const | PRIMARY | PRIMARY | 194 | const | 1 | 100.00 | Using index |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 9 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 8 | JDatabaseDriver->loadResult() | JROOT/libraries/src/Session/MetadataManager.php:74 |
| 7 | Joomla\CMS\Session\MetadataManager->createRecordIfNonExisting() | JROOT/libraries/src/Application/CMSApplication.php:154 |
| 6 | Joomla\CMS\Application\CMSApplication->checkSession() | JROOT/libraries/src/Application/CMSApplication.php:828 |
| 5 | Joomla\CMS\Application\CMSApplication->loadSession() | JROOT/libraries/src/Application/CMSApplication.php:136 |
| 4 | Joomla\CMS\Application\CMSApplication->__construct() | JROOT/libraries/src/Application/SiteApplication.php:66 |
| 3 | Joomla\CMS\Application\SiteApplication->__construct() | JROOT/libraries/src/Application/CMSApplication.php:386 |
| 2 | Joomla\CMS\Application\CMSApplication::getInstance() | JROOT/libraries/src/Factory.php:140 |
| 1 | Joomla\CMS\Factory::getApplication() | JROOT/index.php:46 |
Query Time: 3.46 ms After last query: 0.05 ms Query memory: 0.004 MB Memory before query: 4.273 MB
INSERT INTO `l6r3h_session`
(`session_id`,`guest`,`time`,`userid`,`username`,`client_id`)
VALUES
(X'3531646263363430353462366364323665313164303937653831326134343834', 1, 1713255385, 0, '', 0)
EXPLAIN not possible on query: INSERT INTO `l6r3h_session`
(`session_id`,`guest`,`time`,`userid`,`username`,`client_id`) VALUES
(X'3531646263363430353462366364323665313164303937653831326134343834', 1, 1713255385, 0, '', 0)
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 8 | JDatabaseDriverMysqli->execute() | JROOT/libraries/src/Session/MetadataManager.php:116 |
| 7 | Joomla\CMS\Session\MetadataManager->createRecordIfNonExisting() | JROOT/libraries/src/Application/CMSApplication.php:154 |
| 6 | Joomla\CMS\Application\CMSApplication->checkSession() | JROOT/libraries/src/Application/CMSApplication.php:828 |
| 5 | Joomla\CMS\Application\CMSApplication->loadSession() | JROOT/libraries/src/Application/CMSApplication.php:136 |
| 4 | Joomla\CMS\Application\CMSApplication->__construct() | JROOT/libraries/src/Application/SiteApplication.php:66 |
| 3 | Joomla\CMS\Application\SiteApplication->__construct() | JROOT/libraries/src/Application/CMSApplication.php:386 |
| 2 | Joomla\CMS\Application\CMSApplication::getInstance() | JROOT/libraries/src/Factory.php:140 |
| 1 | Joomla\CMS\Factory::getApplication() | JROOT/index.php:46 |
Query Time: 3.93 ms After last query: 1.64 ms Query memory: 0.081 MB Memory before query: 4.523 MB Rows returned: 56
SELECT `extension_id` AS `id`,`element` AS `option`,`params`,`enabled`
FROM `l6r3h_extensions`
WHERE `type` = 'component'
AND `state` = 0
AND `enabled` = 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_extensions | NULL | ref | extension | extension | 82 | const | 56 | 1.00 | Using where |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 11 | JDatabaseDriver->loadObjectList() | JROOT/libraries/src/Component/ComponentHelper.php:445 |
| 10 | Joomla\CMS\Component\ComponentHelper::Joomla\CMS\Component\{closure}() | Same as call in the line below. |
| 9 | call_user_func_array() | JROOT/libraries/src/Cache/Controller/CallbackController.php:173 |
| 8 | Joomla\CMS\Cache\Controller\CallbackController->get() | JROOT/libraries/src/Component/ComponentHelper.php:453 |
| 7 | Joomla\CMS\Component\ComponentHelper::load() | JROOT/libraries/src/Component/ComponentHelper.php:519 |
| 6 | Joomla\CMS\Component\ComponentHelper::getComponents() | JROOT/libraries/src/Component/ComponentHelper.php:44 |
| 5 | Joomla\CMS\Component\ComponentHelper::getComponent() | JROOT/libraries/src/Component/ComponentHelper.php:103 |
| 4 | Joomla\CMS\Component\ComponentHelper::getParams() | JROOT/libraries/src/Application/SiteApplication.php:594 |
| 3 | Joomla\CMS\Application\SiteApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:212 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.37 ms After last query: 1.59 ms Query memory: 0.021 MB Memory before query: 4.769 MB Rows returned: 6
SELECT id, rules
FROM `l6r3h_viewlevels`
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_viewlevels | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 6 | 100.00 | NULL |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 10 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1506 |
| 9 | JDatabaseDriver->loadAssocList() | JROOT/libraries/src/Access/Access.php:1063 |
| 8 | Joomla\CMS\Access\Access::getAuthorisedViewLevels() | JROOT/libraries/src/User/User.php:458 |
| 7 | Joomla\CMS\User\User->getAuthorisedViewLevels() | JROOT/libraries/src/Plugin/PluginHelper.php:318 |
| 6 | Joomla\CMS\Plugin\PluginHelper::load() | JROOT/libraries/src/Plugin/PluginHelper.php:87 |
| 5 | Joomla\CMS\Plugin\PluginHelper::getPlugin() | JROOT/libraries/src/Plugin/PluginHelper.php:129 |
| 4 | Joomla\CMS\Plugin\PluginHelper::isEnabled() | JROOT/libraries/src/Application/SiteApplication.php:604 |
| 3 | Joomla\CMS\Application\SiteApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:212 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.70 ms After last query: 0.09 ms Query memory: 0.021 MB Memory before query: 4.781 MB Rows returned: 2
SELECT b.id
FROM l6r3h_usergroups AS a
LEFT JOIN l6r3h_usergroups AS b
ON b.lft <= a.lft
AND b.rgt >= a.rgt
WHERE a.id = 11
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | a | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| 1 | SIMPLE | b | NULL | range | idx_usergroup_nested_set_lookup | idx_usergroup_nested_set_lookup | 4 | NULL | 2 | 100.00 | Using where; Using index |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 11 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1550 |
| 10 | JDatabaseDriver->loadColumn() | JROOT/libraries/src/Access/Access.php:980 |
| 9 | Joomla\CMS\Access\Access::getGroupsByUser() | JROOT/libraries/src/Access/Access.php:1095 |
| 8 | Joomla\CMS\Access\Access::getAuthorisedViewLevels() | JROOT/libraries/src/User/User.php:458 |
| 7 | Joomla\CMS\User\User->getAuthorisedViewLevels() | JROOT/libraries/src/Plugin/PluginHelper.php:318 |
| 6 | Joomla\CMS\Plugin\PluginHelper::load() | JROOT/libraries/src/Plugin/PluginHelper.php:87 |
| 5 | Joomla\CMS\Plugin\PluginHelper::getPlugin() | JROOT/libraries/src/Plugin/PluginHelper.php:129 |
| 4 | Joomla\CMS\Plugin\PluginHelper::isEnabled() | JROOT/libraries/src/Application/SiteApplication.php:604 |
| 3 | Joomla\CMS\Application\SiteApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:212 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.84 ms After last query: 0.59 ms Query memory: 0.051 MB Memory before query: 4.850 MB Rows returned: 173
SELECT `folder` AS `type`,`element` AS `name`,`params` AS `params`,`extension_id` AS `id`
FROM l6r3h_extensions
WHERE enabled = 1
AND type = 'plugin'
AND state IN (0,1)
AND access IN (1,1,6)
ORDER BY ordering
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_extensions | NULL | ref | extension | extension | 82 | const | 249 | 0.60 | Using index condition; Using where; Using filesort |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 11 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 10 | JDatabaseDriver->loadObjectList() | JROOT/libraries/src/Plugin/PluginHelper.php:351 |
| 9 | Joomla\CMS\Plugin\PluginHelper::Joomla\CMS\Plugin\{closure}() | Same as call in the line below. |
| 8 | call_user_func_array() | JROOT/libraries/src/Cache/Controller/CallbackController.php:173 |
| 7 | Joomla\CMS\Cache\Controller\CallbackController->get() | JROOT/libraries/src/Plugin/PluginHelper.php:356 |
| 6 | Joomla\CMS\Plugin\PluginHelper::load() | JROOT/libraries/src/Plugin/PluginHelper.php:87 |
| 5 | Joomla\CMS\Plugin\PluginHelper::getPlugin() | JROOT/libraries/src/Plugin/PluginHelper.php:129 |
| 4 | Joomla\CMS\Plugin\PluginHelper::isEnabled() | JROOT/libraries/src/Application/SiteApplication.php:604 |
| 3 | Joomla\CMS\Application\SiteApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:212 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 4.08 ms After last query: 37.22 ms Query memory: 0.101 MB Memory before query: 10.090 MB Rows returned: 73
SELECT m.id, m.menutype, m.title, m.alias, m.note, m.path AS route, m.link, m.type, m.level, m.language,`m`.`browserNav`, m.access, m.params, m.home, m.img, m.template_style_id, m.component_id, m.parent_id,e.element as component
FROM l6r3h_menu AS m
LEFT JOIN l6r3h_extensions AS e
ON m.component_id = e.extension_id
WHERE m.published = 1
AND m.parent_id > 0
AND m.client_id = 0
ORDER BY m.lft
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | m | NULL | ref | idx_client_id_parent_id_alias_language | idx_client_id_parent_id_alias_language | 1 | const | 125 | 3.33 | Using index condition; Using where; Using filesort |
| 1 | SIMPLE | e | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.m.component_id | 1 | 100.00 | Using where |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 31 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 30 | JDatabaseDriver->loadObjectList() | JROOT/libraries/src/Menu/SiteMenu.php:93 |
| 29 | Joomla\CMS\Menu\SiteMenu->Joomla\CMS\Menu\{closure}() | Same as call in the line below. |
| 28 | call_user_func_array() | JROOT/libraries/src/Cache/Controller/CallbackController.php:173 |
| 27 | Joomla\CMS\Cache\Controller\CallbackController->get() | JROOT/libraries/src/Menu/SiteMenu.php:101 |
| 26 | Joomla\CMS\Menu\SiteMenu->load() | JROOT/libraries/src/Menu/AbstractMenu.php:78 |
| 25 | Joomla\CMS\Menu\AbstractMenu->__construct() | JROOT/libraries/src/Menu/SiteMenu.php:62 |
| 24 | Joomla\CMS\Menu\SiteMenu->__construct() | JROOT/libraries/src/Menu/AbstractMenu.php:142 |
| 23 | Joomla\CMS\Menu\AbstractMenu::getInstance() | JROOT/libraries/src/Application/CMSApplication.php:417 |
| 22 | Joomla\CMS\Application\CMSApplication->getMenu() | JROOT/libraries/src/Application/SiteApplication.php:275 |
| 21 | Joomla\CMS\Application\SiteApplication->getMenu() | JROOT/libraries/src/Router/SiteRouter.php:65 |
| 20 | Joomla\CMS\Router\SiteRouter->__construct() | JROOT/libraries/src/Router/Router.php:189 |
| 19 | Joomla\CMS\Router\Router::getInstance() | JROOT/libraries/src/Application/CMSApplication.php:533 |
| 18 | Joomla\CMS\Application\CMSApplication::getRouter() | JROOT/libraries/src/Application/SiteApplication.php:403 |
| 17 | Joomla\CMS\Application\SiteApplication::getRouter() | JROOT/administrator/components/com_sh404sef/vendor/weeblr/wblib/v2/packages/platform/joomla/platform.php:80 |
| 16 | Weeblr\Wblib\V_SH4_4352\Platform\JoomlaPlatform->boot() | JROOT/administrator/components/com_sh404sef/vendor/weeblr/wblib/v2/packages/factory.php:396 |
| 15 | Weeblr\Wblib\V_SH4_4352\Factory->buildPlatform() | JROOT/administrator/components/com_sh404sef/vendor/weeblr/wblib/v2/packages/factory.php:281 |
| 14 | Weeblr\Wblib\V_SH4_4352\Factory->buildObject() | JROOT/administrator/components/com_sh404sef/vendor/weeblr/wblib/v2/packages/factory.php:228 |
| 13 | Weeblr\Wblib\V_SH4_4352\Factory->getObject() | JROOT/administrator/components/com_sh404sef/vendor/weeblr/wblib/v2/packages/factory.php:116 |
| 12 | Weeblr\Wblib\V_SH4_4352\Factory->getThe() | JROOT/administrator/components/com_sh404sef/vendor/weeblr/wblib/v2/packages/system/hook.php:169 |
| 11 | Weeblr\Wblib\V_SH4_4352\System\Hook->execute() | JROOT/administrator/components/com_sh404sef/vendor/weeblr/wblib/v2/packages/system/hook.php:151 |
| 10 | Weeblr\Wblib\V_SH4_4352\System\Hook->filter() | JROOT/administrator/components/com_sh404sef/vendor/weeblr/wblib/v2/wblib.php:136 |
| 9 | Weeblr\Wblib\V_SH4_4352\Wblib->boot() | JROOT/plugins/system/sh404sef/bootstrap.php:43 |
| 8 | include_once JROOT/plugins/system/sh404sef/bootstrap.php | JROOT/plugins/system/sh404sef/sh404sef.php:35 |
| 7 | plgSystemSh404sef->__construct() | JROOT/libraries/src/Plugin/PluginHelper.php:280 |
| 6 | Joomla\CMS\Plugin\PluginHelper::import() | JROOT/libraries/src/Plugin/PluginHelper.php:182 |
| 5 | Joomla\CMS\Plugin\PluginHelper::importPlugin() | JROOT/libraries/src/Application/CMSApplication.php:667 |
| 4 | Joomla\CMS\Application\CMSApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:686 |
| 3 | Joomla\CMS\Application\SiteApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:212 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.73 ms After last query: 20.56 ms Query memory: 0.022 MB Memory before query: 13.300 MB Rows returned: 1
SELECT *
FROM l6r3h_languages
ORDER BY ordering ASC
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_languages | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 1 | 100.00 | Using filesort |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 14 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 13 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_sh404sef/helpers/language.php:219 |
| 12 | Sh404sefHelperLanguage::getAllContentLanguages() | JROOT/administrator/components/com_sh404sef/helpers/language.php:171 |
| 11 | Sh404sefHelperLanguage::getUrlCodeFromTag() | JROOT/administrator/components/com_sh404sef/classes/pageinfo.php:85 |
| 10 | Sh404sefClassPageinfo->setCurrentLanguage() | JROOT/administrator/components/com_sh404sef/classes/pageinfo.php:101 |
| 9 | Sh404sefClassPageinfo->init() | JROOT/plugins/system/sh404sef/sh404sef.php:103 |
| 8 | plgSystemSh404sef->onAfterInitialise() | JROOT/libraries/joomla/event/event.php:70 |
| 7 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 6 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 5 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:668 |
| 4 | Joomla\CMS\Application\CMSApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:686 |
| 3 | Joomla\CMS\Application\SiteApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:212 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.48 ms After last query: 6.21 ms Query memory: 0.062 MB Memory before query: 14.100 MB Rows returned: 1
SELECT `params`
FROM l6r3h_extensions
WHERE `element`='com_sh404sef'
AND `type`='component';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_extensions | NULL | ref | element_clientid,element_folder_clientid,extension | element_clientid | 402 | const | 1 | 10.00 | Using where |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:687 |
| 14 | ShlDbClass->loadResult() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:377 |
| 13 | ShlDbClass->shlLoadResult() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:483 |
| 12 | ShlDbHelper::selectResult() | JROOT/administrator/components/com_sh404sef/helpers/general.php:160 |
| 11 | Sh404sefHelperGeneral::getComponentParams() | JROOT/administrator/components/com_sh404sef/classes/config.php:671 |
| 10 | Sh404sefClassConfig->__construct() | JROOT/administrator/components/com_sh404sef/sh404seffactory.php:121 |
| 9 | Sh404sefFactory::getConfig() | JROOT/plugins/system/sh404sef/sh404sef.php:126 |
| 8 | plgSystemSh404sef->onAfterInitialise() | JROOT/libraries/joomla/event/event.php:70 |
| 7 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 6 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 5 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:668 |
| 4 | Joomla\CMS\Application\CMSApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:686 |
| 3 | Joomla\CMS\Application\SiteApplication->initialiseApp() | JROOT/libraries/src/Application/SiteApplication.php:212 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.56 ms After last query: 21.49 ms Query memory: 0.023 MB Memory before query: 16.978 MB Rows returned: 2
SHOW FULL COLUMNS
FROM `l6r3h_komento_configs`
EXPLAIN not possible on query: SHOW FULL COLUMNS FROM `l6r3h_komento_configs`
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 15 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 14 | JDatabaseDriver->loadObjectList() | JROOT/libraries/joomla/database/driver/mysqli.php:448 |
| 13 | JDatabaseDriverMysqli->getTableColumns() | JROOT/libraries/src/Table/Table.php:261 |
| 12 | Joomla\CMS\Table\Table->getFields() | JROOT/libraries/src/Table/Table.php:585 |
| 11 | Joomla\CMS\Table\Table->reset() | JROOT/libraries/src/Table/Table.php:724 |
| 10 | Joomla\CMS\Table\Table->load() | JROOT/administrator/components/com_komento/includes/komento.php:399 |
| 9 | KT::config() | JROOT/components/com_komento/bootstrap.php:52 |
| 8 | require_once JROOT/components/com_komento/bootstrap.php | JROOT/components/com_komento/router.php:14 |
| 7 | require_once JROOT/components/com_komento/router.php | JROOT/libraries/src/Router/SiteRouter.php:779 |
| 6 | Joomla\CMS\Router\SiteRouter->getComponentRouter() | JROOT/libraries/src/Router/SiteRouter.php:131 |
| 5 | Joomla\CMS\Router\SiteRouter->parse() | JROOT/libraries/src/Application/CMSApplication.php:1142 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.09 ms After last query: 0.08 ms Query memory: 0.022 MB Memory before query: 16.991 MB Rows returned: 1
SELECT *
FROM l6r3h_komento_configs
WHERE `name` = 'config'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_komento_configs | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 3 | 33.33 | Using where |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1465 |
| 11 | JDatabaseDriver->loadAssoc() | JROOT/libraries/src/Table/Table.php:747 |
| 10 | Joomla\CMS\Table\Table->load() | JROOT/administrator/components/com_komento/includes/komento.php:399 |
| 9 | KT::config() | JROOT/components/com_komento/bootstrap.php:52 |
| 8 | require_once JROOT/components/com_komento/bootstrap.php | JROOT/components/com_komento/router.php:14 |
| 7 | require_once JROOT/components/com_komento/router.php | JROOT/libraries/src/Router/SiteRouter.php:779 |
| 6 | Joomla\CMS\Router\SiteRouter->getComponentRouter() | JROOT/libraries/src/Router/SiteRouter.php:131 |
| 5 | Joomla\CMS\Router\SiteRouter->parse() | JROOT/libraries/src/Application/CMSApplication.php:1142 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.30 ms After last query: 5.28 ms Query memory: 0.024 MB Memory before query: 17.539 MB Rows returned: 0
SELECT *
FROM `l6r3h_sh404sef_aliases`
WHERE `state` = 1
and (`alias` = 'Blog/Categories/Miscellaneous/Page-5')
order by `ordering` asc
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_aliases | NULL | ref | state,alias | alias | 573 | const | 1 | 100.00 | Using where; Using filesort |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 17 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 16 | ShlDbClass->loadObject() | JROOT/administrator/components/com_sh404sef/models/redirector.php:222 |
| 15 | Sh404sefModelRedirector->findHardcodedMatchedRules() | JROOT/administrator/components/com_sh404sef/models/redirector.php:116 |
| 14 | Sh404sefModelRedirector->loadMatchRules() | JROOT/administrator/components/com_sh404sef/models/redirector.php:87 |
| 13 | Sh404sefModelRedirector->__construct() | JROOT/administrator/components/com_sh404sef/sh404seffactory.php:205 |
| 12 | Sh404sefFactory::getRedirector() | JROOT/administrator/components/com_sh404sef/classes/router.php:706 |
| 11 | Sh404sefClassRouterInternal->_checkAliases() | JROOT/administrator/components/com_sh404sef/classes/router.php:295 |
| 10 | Sh404sefClassRouterInternal->preprocessParseRule() | Same as call in the line below. |
| 9 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:596 |
| 8 | Joomla\CMS\Router\Router->processParseRules() | JROOT/libraries/src/Router/SiteRouter.php:597 |
| 7 | Joomla\CMS\Router\SiteRouter->processParseRules() | JROOT/libraries/src/Router/Router.php:212 |
| 6 | Joomla\CMS\Router\Router->parse() | JROOT/libraries/src/Router/SiteRouter.php:139 |
| 5 | Joomla\CMS\Router\SiteRouter->parse() | JROOT/libraries/src/Application/CMSApplication.php:1142 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.10 ms After last query: 0.26 ms Query memory: 0.025 MB Memory before query: 17.565 MB Rows returned: 0
SELECT *
FROM l6r3h_sh404sef_aliases
WHERE state = 1
and (type = 1 or type = 2);
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_aliases | NULL | range | type,state | type | 1 | NULL | 2 | 100.00 | Using index condition; Using where |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 20 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 19 | JDatabaseDriver->loadObjectList() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:661 |
| 18 | ShlDbClass->loadObjectList() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:455 |
| 17 | ShlDbClass->shlLoadObjectList() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:686 |
| 16 | ShlDbHelper::selectObjectList() | JROOT/administrator/components/com_sh404sef/models/redirector.php:287 |
| 15 | Sh404sefModelRedirector->findWildcardMatchedRules() | JROOT/administrator/components/com_sh404sef/models/redirector.php:117 |
| 14 | Sh404sefModelRedirector->loadMatchRules() | JROOT/administrator/components/com_sh404sef/models/redirector.php:87 |
| 13 | Sh404sefModelRedirector->__construct() | JROOT/administrator/components/com_sh404sef/sh404seffactory.php:205 |
| 12 | Sh404sefFactory::getRedirector() | JROOT/administrator/components/com_sh404sef/classes/router.php:706 |
| 11 | Sh404sefClassRouterInternal->_checkAliases() | JROOT/administrator/components/com_sh404sef/classes/router.php:295 |
| 10 | Sh404sefClassRouterInternal->preprocessParseRule() | Same as call in the line below. |
| 9 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:596 |
| 8 | Joomla\CMS\Router\Router->processParseRules() | JROOT/libraries/src/Router/SiteRouter.php:597 |
| 7 | Joomla\CMS\Router\SiteRouter->processParseRules() | JROOT/libraries/src/Router/Router.php:212 |
| 6 | Joomla\CMS\Router\Router->parse() | JROOT/libraries/src/Router/SiteRouter.php:139 |
| 5 | Joomla\CMS\Router\SiteRouter->parse() | JROOT/libraries/src/Application/CMSApplication.php:1142 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.13 ms After last query: 0.05 ms Query memory: 0.023 MB Memory before query: 17.573 MB Rows returned: 0
SELECT *
FROM l6r3h_sh404sef_pageids
WHERE `pageid`='Blog/Categories/Miscellaneous/Page-5';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_pageids | NULL | ref | alias | alias | 767 | const | 1 | 100.00 | NULL |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 15 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 14 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 13 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 12 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/classes/router.php:2357 |
| 11 | Sh404sefClassRouterInternal->_checkShurls() | JROOT/administrator/components/com_sh404sef/classes/router.php:296 |
| 10 | Sh404sefClassRouterInternal->preprocessParseRule() | Same as call in the line below. |
| 9 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:596 |
| 8 | Joomla\CMS\Router\Router->processParseRules() | JROOT/libraries/src/Router/SiteRouter.php:597 |
| 7 | Joomla\CMS\Router\SiteRouter->processParseRules() | JROOT/libraries/src/Router/Router.php:212 |
| 6 | Joomla\CMS\Router\Router->parse() | JROOT/libraries/src/Router/SiteRouter.php:139 |
| 5 | Joomla\CMS\Router\SiteRouter->parse() | JROOT/libraries/src/Application/CMSApplication.php:1142 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.20 ms After last query: 0.18 ms Query memory: 0.024 MB Memory before query: 17.585 MB Rows returned: 1
SELECT *
FROM l6r3h_languages
WHERE published=1
ORDER BY ordering ASC
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_languages | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 1 | 100.00 | Using where; Using filesort |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 19 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 18 | JDatabaseDriver->loadObjectList() | JROOT/libraries/src/Language/LanguageHelper.php:150 |
| 17 | Joomla\CMS\Language\LanguageHelper::getLanguages() | JROOT/administrator/components/com_sh404sef/classes/router.php:2067 |
| 16 | Sh404sefClassRouterInternal->_getSimpleSefLanguageSefCode() | JROOT/administrator/components/com_sh404sef/classes/router.php:2035 |
| 15 | Sh404sefClassRouterInternal->_isSimpleEncodingSef() | JROOT/administrator/components/com_sh404sef/classes/router.php:1978 |
| 14 | Sh404sefClassRouterInternal->_lookupSef() | JROOT/administrator/components/com_sh404sef/classes/router.php:1439 |
| 13 | Sh404sefClassRouterInternal->_parseSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2664 |
| 12 | Sh404sefClassRouter->_parseSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:457 |
| 11 | Sh404sefClassRouterInternal->parseRule() | Same as call in the line below. |
| 10 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:596 |
| 9 | Joomla\CMS\Router\Router->processParseRules() | JROOT/libraries/src/Router/SiteRouter.php:597 |
| 8 | Joomla\CMS\Router\SiteRouter->processParseRules() | JROOT/libraries/src/Router/Router.php:570 |
| 7 | Joomla\CMS\Router\Router->_processParseRules() | JROOT/libraries/src/Router/Router.php:216 |
| 6 | Joomla\CMS\Router\Router->parse() | JROOT/libraries/src/Router/SiteRouter.php:139 |
| 5 | Joomla\CMS\Router\SiteRouter->parse() | JROOT/libraries/src/Application/CMSApplication.php:1142 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.66 ms After last query: 1.32 ms Query memory: 0.026 MB Memory before query: 17.699 MB Rows returned: 4
SELECT `oldurl`, `newurl`, `dateadd`, `id`, `cpt`, `rank`
FROM l6r3h_sh404sef_urls
WHERE `oldurl`='Blog/Categories/Miscellaneous/Page-5'
ORDER BY `rank`;
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | oldurl | oldurl | 573 | const | 4 | 100.00 | Using where; Using filesort |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 20 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 19 | JDatabaseDriver->loadObjectList() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:661 |
| 18 | ShlDbClass->loadObjectList() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:455 |
| 17 | ShlDbClass->shlLoadObjectList() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:686 |
| 16 | ShlDbHelper::selectObjectList() | JROOT/administrator/components/com_sh404sef/models/sefurls.php:103 |
| 15 | Sh404sefModelSefurls->getNonSefUrlRecordFromDatabase() | JROOT/administrator/components/com_sh404sef/classes/router.php:1992 |
| 14 | Sh404sefClassRouterInternal->_lookupSef() | JROOT/administrator/components/com_sh404sef/classes/router.php:1439 |
| 13 | Sh404sefClassRouterInternal->_parseSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2664 |
| 12 | Sh404sefClassRouter->_parseSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:457 |
| 11 | Sh404sefClassRouterInternal->parseRule() | Same as call in the line below. |
| 10 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:596 |
| 9 | Joomla\CMS\Router\Router->processParseRules() | JROOT/libraries/src/Router/SiteRouter.php:597 |
| 8 | Joomla\CMS\Router\SiteRouter->processParseRules() | JROOT/libraries/src/Router/Router.php:570 |
| 7 | Joomla\CMS\Router\Router->_processParseRules() | JROOT/libraries/src/Router/Router.php:216 |
| 6 | Joomla\CMS\Router\Router->parse() | JROOT/libraries/src/Router/SiteRouter.php:139 |
| 5 | Joomla\CMS\Router\SiteRouter->parse() | JROOT/libraries/src/Application/CMSApplication.php:1142 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 4.03 ms After last query: 0.44 ms Query memory: 0.008 MB Memory before query: 17.732 MB
UPDATE `l6r3h_sh404sef_urls`
SET `cpt`=924, `last_hit`='2024-04-16 08:16:26'
WHERE `id`='83292'
AND `rank`=0;
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | UPDATE | l6r3h_sh404sef_urls | NULL | range | PRIMARY,rank | PRIMARY | 4 | const | 1 | 100.00 | Using where |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/plugins/system/shlib/shl_packages/system/abstractdecorator.php:41 |
| 17 | ShlSystem_Abstractdecorator->__call() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:478 |
| 16 | ShlDbClass->shlExecute() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:467 |
| 15 | ShlDbClass->shlQuery() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:797 |
| 14 | ShlDbHelper::update() | JROOT/administrator/components/com_sh404sef/classes/router.php:1458 |
| 13 | Sh404sefClassRouterInternal->_parseSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2664 |
| 12 | Sh404sefClassRouter->_parseSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:457 |
| 11 | Sh404sefClassRouterInternal->parseRule() | Same as call in the line below. |
| 10 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:596 |
| 9 | Joomla\CMS\Router\Router->processParseRules() | JROOT/libraries/src/Router/SiteRouter.php:597 |
| 8 | Joomla\CMS\Router\SiteRouter->processParseRules() | JROOT/libraries/src/Router/Router.php:570 |
| 7 | Joomla\CMS\Router\Router->_processParseRules() | JROOT/libraries/src/Router/Router.php:216 |
| 6 | Joomla\CMS\Router\Router->parse() | JROOT/libraries/src/Router/SiteRouter.php:139 |
| 5 | Joomla\CMS\Router\SiteRouter->parse() | JROOT/libraries/src/Application/CMSApplication.php:1142 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.74 ms After last query: 3.00 ms Query memory: 0.021 MB Memory before query: 17.995 MB Rows returned: 1
SELECT COUNT(*)
FROM l6r3h_rantispam_banip
WHERE bannedip = '3.138.138.144'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | NULL | NULL | NULL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | NULL | NULL | no matching row in const table |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 11 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 10 | JDatabaseDriver->loadResult() | JROOT/plugins/system/rantispam/rantispam.php:87 |
| 9 | plgSystemRAntiSpam->checkBanned() | JROOT/plugins/system/rantispam/rantispam.php:121 |
| 8 | plgSystemRAntiSpam->onAfterRoute() | JROOT/libraries/joomla/event/event.php:70 |
| 7 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 6 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 5 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1190 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 3.76 ms After last query: 0.16 ms Query memory: 0.027 MB Memory before query: 18.008 MB Rows returned: 56
SELECT `id`,`name`,`rules`,`parent_id`
FROM `l6r3h_assets`
WHERE `name` IN ('root.1','com_actionlogs','com_acymailing','com_acysms','com_admin','com_admintools','com_ajax','com_akeeba','com_associations','com_banners','com_cache','com_categories','com_checkin','com_config','com_contact','com_content','com_contenthistory','com_cpanel','com_ctransifex','com_docimport','com_easyblog','com_fields','com_finder','com_installer','com_ipmapping','com_issuetracker','com_jce','com_joomlaupdate','com_jotcache','com_kbase','com_komento','com_kunena','com_languages','com_login','com_mailto','com_media','com_menus','com_messages','com_modules','com_newsfeeds','com_osmap','com_osmeta','com_phocadownload','com_plugins','com_postinstall','com_privacy','com_quicklogout','com_rantispam','com_redirect','com_rquote','com_search','com_sh404sef','com_tags','com_templates','com_users','com_weblinks','com_wrapper')
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_assets | NULL | range | idx_asset_name | idx_asset_name | 202 | NULL | 57 | 100.00 | Using index condition |
No SHOW PROFILE (maybe because there are more than 100 queries)
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 15 | JDatabaseDriver->loadObjectList() | JROOT/libraries/src/Access/Access.php:429 |
| 14 | Joomla\CMS\Access\Access::preloadComponents() | JROOT/libraries/src/Access/Access.php:213 |
| 13 | Joomla\CMS\Access\Access::preload() | JROOT/libraries/src/Access/Access.php:531 |
| 12 | Joomla\CMS\Access\Access::getAssetRules() | JROOT/libraries/src/Access/Access.php:183 |
| 11 | Joomla\CMS\Access\Access::check() | JROOT/libraries/src/User/User.php:398 |
| 10 | Joomla\CMS\User\User->authorise() | JROOT/plugins/system/rantispam/rantispam.php:110 |
| 9 | plgSystemRAntiSpam->canSubmitAnything() | JROOT/plugins/system/rantispam/rantispam.php:123 |
| 8 | plgSystemRAntiSpam->onAfterRoute() | JROOT/libraries/joomla/event/event.php:70 |
| 7 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 6 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 5 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1190 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.59 ms After last query: 4.50 ms Query memory: 0.024 MB Memory before query: 18.634 MB Rows returned: 37
SELECT *
FROM l6r3h_acysms_config
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_acysms_config | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 37 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.09 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.16 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.09 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 14 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 13 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_acysms/classes/cpanel.php:17 |
| 12 | ACYSMScpanelClass->load() | JROOT/administrator/components/com_acysms/helpers/helper.php:265 |
| 11 | ACYSMS::config() | JROOT/administrator/components/com_acysms/helpers/helper.php:774 |
| 10 | include_once JROOT/administrator/components/com_acysms/helpers/helper.php | JROOT/plugins/system/acysmsverifnumber/acysmsverifnumber.php:30 |
| 9 | plgSystemAcySMSVerifNumber->init() | JROOT/plugins/system/acysmsverifnumber/acysmsverifnumber.php:48 |
| 8 | plgSystemAcySMSVerifNumber->onAfterRoute() | JROOT/libraries/joomla/event/event.php:70 |
| 7 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 6 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 5 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1190 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.22 ms After last query: 2.96 ms Query memory: 0.025 MB Memory before query: 19.020 MB Rows returned: 3
SELECT id, home, template, s.params
FROM l6r3h_template_styles as s
LEFT JOIN l6r3h_extensions as e
ON e.element=s.template
AND e.type='template'
AND e.client_id=s.client_id
WHERE s.client_id = 0
AND e.enabled = 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | e | NULL | ref | element_clientid,element_folder_clientid,extension | extension | 82 | const | 5 | 1.00 | Using index condition; Using where |
| 1 | SIMPLE | s | NULL | ref | idx_template,idx_client_id,idx_client_id_home | idx_template | 202 | db597855425.e.element | 1 | 60.00 | Using index condition; Using where |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.07 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.07 ms |
| preparing | 0.02 ms |
| executing | 0.00 ms |
| Sending data | 0.07 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 21 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 20 | JDatabaseDriver->loadObjectList() | JROOT/libraries/src/Application/SiteApplication.php:486 |
| 19 | Joomla\CMS\Application\SiteApplication->getTemplate() | JROOT/libraries/src/HTML/HTMLHelper.php:365 |
| 18 | Joomla\CMS\HTML\HTMLHelper::includeRelativeFiles() | JROOT/libraries/src/HTML/HTMLHelper.php:712 |
| 17 | Joomla\CMS\HTML\HTMLHelper::script() | Same as call in the line below. |
| 16 | call_user_func_array() | JROOT/libraries/src/HTML/HTMLHelper.php:239 |
| 15 | Joomla\CMS\HTML\HTMLHelper::call() | JROOT/libraries/src/HTML/HTMLHelper.php:146 |
| 14 | Joomla\CMS\HTML\HTMLHelper::_() | JROOT/libraries/cms/html/behavior.php:63 |
| 13 | JHtmlBehavior::framework() | Same as call in the line below. |
| 12 | call_user_func_array() | JROOT/libraries/src/HTML/HTMLHelper.php:239 |
| 11 | Joomla\CMS\HTML\HTMLHelper::call() | JROOT/libraries/src/HTML/HTMLHelper.php:146 |
| 10 | Joomla\CMS\HTML\HTMLHelper::_() | JROOT/administrator/components/com_acysms/compat/compat3.php:35 |
| 9 | acysms_loadMootools() | JROOT/plugins/system/acysmsverifnumber/acysmsverifnumber.php:49 |
| 8 | plgSystemAcySMSVerifNumber->onAfterRoute() | JROOT/libraries/joomla/event/event.php:70 |
| 7 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 6 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 5 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1190 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.00 ms After last query: 0.55 ms Query memory: 0.028 MB Memory before query: 19.073 MB Rows returned: 1
SELECT `extension_id` AS `id`,`element` AS `option`,`params`,`enabled`
FROM `l6r3h_extensions`
WHERE `type` = 'library'
AND `element` = 'joomla'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_extensions | NULL | ref | element_clientid,element_folder_clientid,extension | extension | 484 | const,const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.05 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 28 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 27 | JDatabaseDriver->loadObject() | JROOT/libraries/src/Helper/LibraryHelper.php:167 |
| 26 | Joomla\CMS\Helper\LibraryHelper::Joomla\CMS\Helper\{closure}() | Same as call in the line below. |
| 25 | call_user_func_array() | JROOT/libraries/src/Cache/Controller/CallbackController.php:173 |
| 24 | Joomla\CMS\Cache\Controller\CallbackController->get() | JROOT/libraries/src/Helper/LibraryHelper.php:175 |
| 23 | Joomla\CMS\Helper\LibraryHelper::loadLibrary() | JROOT/libraries/src/Helper/LibraryHelper.php:43 |
| 22 | Joomla\CMS\Helper\LibraryHelper::getLibrary() | JROOT/libraries/src/Helper/LibraryHelper.php:90 |
| 21 | Joomla\CMS\Helper\LibraryHelper::getParams() | JROOT/libraries/src/Version.php:321 |
| 20 | Joomla\CMS\Version->getMediaVersion() | JROOT/libraries/src/Factory.php:778 |
| 19 | Joomla\CMS\Factory::createDocument() | JROOT/libraries/src/Factory.php:234 |
| 18 | Joomla\CMS\Factory::getDocument() | JROOT/libraries/src/HTML/HTMLHelper.php:731 |
| 17 | Joomla\CMS\HTML\HTMLHelper::script() | Same as call in the line below. |
| 16 | call_user_func_array() | JROOT/libraries/src/HTML/HTMLHelper.php:239 |
| 15 | Joomla\CMS\HTML\HTMLHelper::call() | JROOT/libraries/src/HTML/HTMLHelper.php:146 |
| 14 | Joomla\CMS\HTML\HTMLHelper::_() | JROOT/libraries/cms/html/behavior.php:63 |
| 13 | JHtmlBehavior::framework() | Same as call in the line below. |
| 12 | call_user_func_array() | JROOT/libraries/src/HTML/HTMLHelper.php:239 |
| 11 | Joomla\CMS\HTML\HTMLHelper::call() | JROOT/libraries/src/HTML/HTMLHelper.php:146 |
| 10 | Joomla\CMS\HTML\HTMLHelper::_() | JROOT/administrator/components/com_acysms/compat/compat3.php:35 |
| 9 | acysms_loadMootools() | JROOT/plugins/system/acysmsverifnumber/acysmsverifnumber.php:49 |
| 8 | plgSystemAcySMSVerifNumber->onAfterRoute() | JROOT/libraries/joomla/event/event.php:70 |
| 7 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 6 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 5 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1190 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 3.12 ms After last query: 0.09 ms Query memory: 0.010 MB Memory before query: 19.069 MB
UPDATE `l6r3h_extensions`
SET `params` = '{\"mediaversion\":\"71ba84aaa326bc844076bdb64dffd081\"}'
WHERE `type` = 'library'
AND `element` = 'joomla'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | UPDATE | l6r3h_extensions | NULL | range | element_clientid,element_folder_clientid,extension | extension | 484 | const,const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.02 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.05 ms |
| updating | 0.06 ms |
| end | 0.01 ms |
| query end | 2.11 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 23 | JDatabaseDriverMysqli->execute() | JROOT/libraries/src/Helper/LibraryHelper.php:117 |
| 22 | Joomla\CMS\Helper\LibraryHelper::saveParams() | JROOT/libraries/src/Version.php:372 |
| 21 | Joomla\CMS\Version->setMediaVersion() | JROOT/libraries/src/Version.php:331 |
| 20 | Joomla\CMS\Version->getMediaVersion() | JROOT/libraries/src/Factory.php:778 |
| 19 | Joomla\CMS\Factory::createDocument() | JROOT/libraries/src/Factory.php:234 |
| 18 | Joomla\CMS\Factory::getDocument() | JROOT/libraries/src/HTML/HTMLHelper.php:731 |
| 17 | Joomla\CMS\HTML\HTMLHelper::script() | Same as call in the line below. |
| 16 | call_user_func_array() | JROOT/libraries/src/HTML/HTMLHelper.php:239 |
| 15 | Joomla\CMS\HTML\HTMLHelper::call() | JROOT/libraries/src/HTML/HTMLHelper.php:146 |
| 14 | Joomla\CMS\HTML\HTMLHelper::_() | JROOT/libraries/cms/html/behavior.php:63 |
| 13 | JHtmlBehavior::framework() | Same as call in the line below. |
| 12 | call_user_func_array() | JROOT/libraries/src/HTML/HTMLHelper.php:239 |
| 11 | Joomla\CMS\HTML\HTMLHelper::call() | JROOT/libraries/src/HTML/HTMLHelper.php:146 |
| 10 | Joomla\CMS\HTML\HTMLHelper::_() | JROOT/administrator/components/com_acysms/compat/compat3.php:35 |
| 9 | acysms_loadMootools() | JROOT/plugins/system/acysmsverifnumber/acysmsverifnumber.php:49 |
| 8 | plgSystemAcySMSVerifNumber->onAfterRoute() | JROOT/libraries/joomla/event/event.php:70 |
| 7 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 6 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 5 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1190 |
| 4 | Joomla\CMS\Application\CMSApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:796 |
| 3 | Joomla\CMS\Application\SiteApplication->route() | JROOT/libraries/src/Application/SiteApplication.php:218 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.56 ms After last query: 7.72 ms Query memory: 0.092 MB Memory before query: 20.239 MB Rows returned: 1
SELECT *
FROM l6r3h_easyblog_configs
WHERE `name` = 'config'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_configs | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 4 | 25.00 | Using where |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.26 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.17 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1465 |
| 11 | JDatabaseDriver->loadAssoc() | JROOT/libraries/src/Table/Table.php:747 |
| 10 | Joomla\CMS\Table\Table->load() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:536 |
| 9 | EB::config() | JROOT/components/com_easyblog/services/cron.php:16 |
| 8 | require_once JROOT/components/com_easyblog/services/cron.php | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3436 |
| 7 | EB::loadServices() | JROOT/components/com_easyblog/easyblog.php:34 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.87 ms After last query: 5.06 ms Query memory: 0.023 MB Memory before query: 20.951 MB Rows returned: 0
SELECT *
FROM `l6r3h_easyblog_post`
WHERE `publish_up`<='2024-04-16 08:16:26'
AND `published`='2'
AND `state`='0'
ORDER BY `id`
LIMIT 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_post | NULL | ref | easyblog_post_published,easyblog_post_blogger_list,easyblog_frontpage1,idx_pre_soucetype_postcount,idx_post_sql1,idx_latest_posts | easyblog_post_published | 1 | const | 1 | 5.00 | Using index condition; Using where |
| Status | Duration |
|---|
| starting | 0.07 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.50 ms |
| init | 0.07 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.11 ms |
| preparing | 0.03 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.08 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 12 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 11 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/blogs.php:389 |
| 10 | EasyBlogModelBlogs->getScheduledPosts() | JROOT/administrator/components/com_easyblog/includes/scheduler/scheduler.php:55 |
| 9 | EasyBlogScheduler->publish() | JROOT/components/com_easyblog/services/maintenance.php:22 |
| 8 | require_once JROOT/components/com_easyblog/services/maintenance.php | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3436 |
| 7 | EB::loadServices() | JROOT/components/com_easyblog/easyblog.php:34 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.71 ms After last query: 4.11 ms Query memory: 0.022 MB Memory before query: 22.053 MB Rows returned: 0
SELECT id, created_by
FROM`l6r3h_easyblog_post`
WHERE `publish_down` > `publish_up`
AND `publish_down` <= '2024-04-16 08:16:26'
AND `publish_down` != '0000-00-00 00:00:00'
AND `published` = '1'
AND `state` = '0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_post | NULL | range | easyblog_post_published,easyblog_post_blogger_list,easyblog_frontpage1,idx_pre_soucetype_postcount,idx_post_sql1,idx_publishdown_posts,idx_latest_posts | idx_publishdown_posts | 11 | NULL | 2 | 3.33 | Using index condition; Using where |
| Status | Duration |
|---|
| starting | 0.07 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.23 ms |
| System lock | 0.02 ms |
| optimizing | 0.02 ms |
| statistics | 0.31 ms |
| preparing | 0.03 ms |
| executing | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 12 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 11 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/blogs.php:545 |
| 10 | EasyBlogModelBlogs->getUnpublishScheduledPosts() | JROOT/administrator/components/com_easyblog/includes/scheduler/scheduler.php:26 |
| 9 | EasyBlogScheduler->unpublish() | JROOT/components/com_easyblog/services/maintenance.php:25 |
| 8 | require_once JROOT/components/com_easyblog/services/maintenance.php | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3436 |
| 7 | EB::loadServices() | JROOT/components/com_easyblog/easyblog.php:34 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.55 ms After last query: 0.07 ms Query memory: 0.022 MB Memory before query: 22.059 MB Rows returned: 0
SELECT *
FROM `l6r3h_easyblog_uploader_tmp`
WHERE `created` <= DATE_SUB('2024-04-16 08:16:26' , INTERVAL 120 MINUTE)
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_uploader_tmp | NULL | range | idx_uploader_created | idx_uploader_created | 5 | NULL | 1 | 100.00 | Using index condition |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.41 ms |
| init | 0.05 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.06 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 11 | JDatabaseDriver->loadObject() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 10 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/includes/scheduler/scheduler.php:168 |
| 9 | EasyBlogScheduler->removeTmpFiles() | JROOT/components/com_easyblog/services/maintenance.php:28 |
| 8 | require_once JROOT/components/com_easyblog/services/maintenance.php | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3436 |
| 7 | EB::loadServices() | JROOT/components/com_easyblog/easyblog.php:34 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.50 ms After last query: 0.06 ms Query memory: 0.022 MB Memory before query: 22.066 MB Rows returned: 0
SELECT a.`id`
FROM `l6r3h_easyblog_post` as a
inner join `l6r3h_easyblog_revisions` as b
on a.`id` = b.`post_id`
where a.`published` = '9'
and a.`created` <= DATE_SUB('2024-04-16 08:16:26', INTERVAL 3 DAY)
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | a | NULL | ref | PRIMARY,easyblog_post_published,easyblog_post_blogger_list,easyblog_frontpage1,idx_pre_soucetype_postcount,idx_post_sql1,idx_latest_posts | easyblog_post_published | 1 | const | 1 | 33.33 | Using where |
| 1 | SIMPLE | b | NULL | ref | idx_postid,idx_ordering,idx_revision_state | idx_postid | 8 | db597855425.a.id | 1 | 100.00 | Using where; Using index |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.22 ms |
| init | 0.04 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.11 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 11 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 10 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/includes/scheduler/scheduler.php:210 |
| 9 | EasyBlogScheduler->removeBlankPosts() | JROOT/components/com_easyblog/services/maintenance.php:31 |
| 8 | require_once JROOT/components/com_easyblog/services/maintenance.php | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3436 |
| 7 | EB::loadServices() | JROOT/components/com_easyblog/easyblog.php:34 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.32 ms After last query: 0.05 ms Query memory: 0.006 MB Memory before query: 22.072 MB
DELETE a, b
FROM `l6r3h_easyblog_post` as a
inner join `l6r3h_easyblog_revisions` as b
on a.`id` = b.`post_id`
where a.`published` = '9'
and a.`created` <= DATE_SUB('2024-04-16 08:16:26', INTERVAL 3 DAY)
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | DELETE | a | NULL | ref | PRIMARY,easyblog_post_published,easyblog_post_blogger_list,easyblog_frontpage1,idx_pre_soucetype_postcount,idx_post_sql1,idx_latest_posts | easyblog_post_published | 1 | const | 1 | 33.33 | Using where |
| 1 | DELETE | b | NULL | ref | idx_postid,idx_ordering,idx_revision_state | idx_postid | 8 | db597855425.a.id | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| init | 0.03 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| deleting from main table | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.09 ms |
| preparing | 0.03 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| deleting from reference tables | 0.01 ms |
| end | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 11 | JDatabaseDriverMysqli->execute() | JROOT/administrator/components/com_easyblog/includes/utils.php:164 |
| 10 | EasyBlogDbJoomla->query() | JROOT/administrator/components/com_easyblog/includes/scheduler/scheduler.php:223 |
| 9 | EasyBlogScheduler->removeBlankPosts() | JROOT/components/com_easyblog/services/maintenance.php:31 |
| 8 | require_once JROOT/components/com_easyblog/services/maintenance.php | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3436 |
| 7 | EB::loadServices() | JROOT/components/com_easyblog/easyblog.php:34 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.23 ms After last query: 2.06 ms Query memory: 0.023 MB Memory before query: 22.382 MB Rows returned: 1
SELECT *
FROM `l6r3h_menu`
WHERE `published`='1'
AND `link` LIKE 'index.php?option=com_easyblog%'
AND `client_id` = '0'
ORDER BY `id`
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_menu | NULL | ref | idx_client_id_parent_id_alias_language | idx_client_id_parent_id_alias_language | 1 | const | 100 | 1.11 | Using index condition; Using where; Using filesort |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.04 ms |
| init | 0.14 ms |
| System lock | 0.02 ms |
| optimizing | 0.10 ms |
| statistics | 0.14 ms |
| preparing | 0.03 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| Creating sort index | 0.63 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 15 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 14 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 13 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/menu.php:44 |
| 12 | EasyBlogModelMenu->getAssociatedMenus() | JROOT/administrator/components/com_easyblog/includes/router.php:97 |
| 11 | EBR::getMenus() | JROOT/administrator/components/com_easyblog/includes/router.php:533 |
| 10 | EBR::_() | JROOT/administrator/components/com_easyblog/includes/router.php:1099 |
| 9 | EBR::getRoutedURL() | JROOT/components/com_easyblog/services/weblog.php:26 |
| 8 | require_once JROOT/components/com_easyblog/services/weblog.php | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3436 |
| 7 | EB::loadServices() | JROOT/components/com_easyblog/easyblog.php:34 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.20 ms After last query: 6.89 ms Query memory: 0.029 MB Memory before query: 23.175 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_easyblog&Itemid=486&lang=en&tmpl=component&view=rsd';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.07 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 29 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 28 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 27 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 26 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 25 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 24 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 23 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 22 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 21 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 20 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 19 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 18 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 17 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 16 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 15 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 14 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 13 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 12 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 11 | Joomla\CMS\Router\Route::_() | JROOT/administrator/components/com_easyblog/includes/router.php:788 |
| 10 | EBR::_() | JROOT/administrator/components/com_easyblog/includes/router.php:1099 |
| 9 | EBR::getRoutedURL() | JROOT/components/com_easyblog/services/weblog.php:26 |
| 8 | require_once JROOT/components/com_easyblog/services/weblog.php | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3436 |
| 7 | EB::loadServices() | JROOT/components/com_easyblog/easyblog.php:34 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.31 ms After last query: 2.74 ms Query memory: 0.031 MB Memory before query: 23.427 MB Rows returned: 1
SELECT `oldurl`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_easyblog&Itemid=486&lang=en&view=rsd';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.06 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 31 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 30 | JDatabaseDriver->loadResult() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:687 |
| 29 | ShlDbClass->loadResult() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:377 |
| 28 | ShlDbClass->shlLoadResult() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:483 |
| 27 | ShlDbHelper::selectResult() | JROOT/components/com_sh404sef/sef_ext.php:962 |
| 26 | sef_404::sefGetLocation() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:519 |
| 25 | shFinalizePlugin() | JROOT/components/com_easyblog/sef_ext/com_easyblog.php:97 |
| 24 | include JROOT/components/com_easyblog/sef_ext/com_easyblog.php | JROOT/components/com_sh404sef/sef_ext.php:388 |
| 23 | sef_404->create() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1798 |
| 22 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 21 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 20 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 19 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 18 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 17 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 16 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 15 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 14 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 13 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 12 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 11 | Joomla\CMS\Router\Route::_() | JROOT/administrator/components/com_easyblog/includes/router.php:788 |
| 10 | EBR::_() | JROOT/administrator/components/com_easyblog/includes/router.php:1099 |
| 9 | EBR::getRoutedURL() | JROOT/components/com_easyblog/services/weblog.php:26 |
| 8 | require_once JROOT/components/com_easyblog/services/weblog.php | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3436 |
| 7 | EB::loadServices() | JROOT/components/com_easyblog/easyblog.php:34 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.55 ms After last query: 1.12 ms Query memory: 0.031 MB Memory before query: 23.577 MB Rows returned: 51
SELECT *
FROM `l6r3h_easyblog_acl`
WHERE `published`='1'
ORDER BY `id` ASC
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_acl | NULL | index | idx_acl_published,idx_acl_published_id | PRIMARY | 8 | NULL | 51 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.24 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.02 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.14 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.06 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 14 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 13 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 12 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/includes/acl/acl.php:329 |
| 11 | EasyBlogAcl::getRules() | JROOT/administrator/components/com_easyblog/includes/acl/acl.php:36 |
| 10 | EasyBlogAcl::getRuleSet() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:298 |
| 9 | EB::acl() | JROOT/components/com_easyblog/controllers/controller.php:20 |
| 8 | EasyBlogController->__construct() | JROOT/libraries/src/MVC/Controller/BaseController.php:313 |
| 7 | Joomla\CMS\MVC\Controller\BaseController::getInstance() | JROOT/components/com_easyblog/easyblog.php:42 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.71 ms After last query: 0.09 ms Query memory: 0.032 MB Memory before query: 23.615 MB Rows returned: 102
SELECT *
FROM `l6r3h_easyblog_acl_group`
WHERE `content_id` IN (1, 11)
AND `type`='
group'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_acl_group | NULL | ALL | easyblog_post_acl_content_type | NO INDEX KEY COULD BE USED | NULL | NULL | 561 | 18.18 | Using where |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.20 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.05 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.45 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 14 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 13 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 12 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/includes/acl/acl.php:151 |
| 11 | EasyBlogAcl::getEasyBlogAclGroups() | JROOT/administrator/components/com_easyblog/includes/acl/acl.php:98 |
| 10 | EasyBlogAcl::getRuleSet() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:298 |
| 9 | EB::acl() | JROOT/components/com_easyblog/controllers/controller.php:20 |
| 8 | EasyBlogController->__construct() | JROOT/libraries/src/MVC/Controller/BaseController.php:313 |
| 7 | Joomla\CMS\MVC\Controller\BaseController::getInstance() | JROOT/components/com_easyblog/easyblog.php:42 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.06 ms After last query: 3.04 ms Query memory: 0.024 MB Memory before query: 23.946 MB Rows returned: 0
SELECT `id`
FROM `l6r3h_menu`
WHERE ( `link`='index.php?option=com_easyblog&view=categories&layout=listings&id=9' OR `link` LIKE 'index.php?option=com_easyblog&view=categories&layout=listings&id=9&
limit%' OR `link`='index.php?option=com_easyblog&view=categories&layout=listings&id=9' )
AND `published`='1'
AND (`language`='en-GB' OR `language`='' OR `language`='*')
LIMIT 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_menu | NULL | ALL | idx_language | NO INDEX KEY COULD BE USED | NULL | NULL | 251 | 2.80 | Using where |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.08 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.87 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 17 | JDatabaseDriver->loadResult() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 16 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/menu.php:324 |
| 15 | EasyBlogModelMenu->getMenusByCategoryId() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3810 |
| 14 | EB::getMenuParams() | JROOT/components/com_easyblog/views/categories/view.html.php:50 |
| 13 | EasyBlogViewCategories->defineParams() | JROOT/components/com_easyblog/views/views.php:53 |
| 12 | EasyBlogView->__construct() | JROOT/libraries/src/MVC/Factory/LegacyFactory.php:89 |
| 11 | Joomla\CMS\MVC\Factory\LegacyFactory->createView() | JROOT/libraries/src/MVC/Controller/BaseController.php:590 |
| 10 | Joomla\CMS\MVC\Controller\BaseController->createView() | JROOT/libraries/src/MVC/Controller/BaseController.php:833 |
| 9 | Joomla\CMS\MVC\Controller\BaseController->getView() | JROOT/components/com_easyblog/controllers/controller.php:67 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.67 ms After last query: 1.65 ms Query memory: 0.022 MB Memory before query: 24.131 MB Rows returned: 1
SELECT *
FROM l6r3h_easyblog_category
WHERE `id` = '9'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_category | NULL | const | PRIMARY | PRIMARY | 8 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.45 ms |
| init | 0.04 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1465 |
| 11 | JDatabaseDriver->loadAssoc() | JROOT/libraries/src/Table/Table.php:747 |
| 10 | Joomla\CMS\Table\Table->load() | JROOT/components/com_easyblog/views/categories/view.html.php:148 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 4.69 ms After last query: 10.96 ms Query memory: 0.023 MB Memory before query: 25.696 MB Rows returned: 1
SELECT COUNT(1)
FROM `l6r3h_easyblog_category_acl` as a
LEFT JOIN `l6r3h_easyblog_category` as b
ON a.`category_id` = b.`id`
WHERE b.`published` = '1'
AND a.`acl_id` = '2'
AND a.`type` = 'user'
AND a.`content_id` = ''
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | a | NULL | ref | easyblog_category_acl,easyblog_category_acl_id,easyblog_content_type,easyblog_category_content_type,idx_cat_post_acl | easyblog_category_acl_id | 8 | const | 1 | 100.00 | Using index condition; Using where |
| 1 | SIMPLE | b | NULL | eq_ref | PRIMARY,easyblog_cat_published,idx_category_access | PRIMARY | 8 | db597855425.a.category_id | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.15 ms |
| checking permissions | 0.02 ms |
| checking permissions | 0.04 ms |
| Opening tables | 0.46 ms |
| init | 0.07 ms |
| System lock | 0.02 ms |
| optimizing | 0.03 ms |
| statistics | 0.17 ms |
| preparing | 0.04 ms |
| executing | 0.02 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.02 ms |
| closing tables | 0.02 ms |
| freeing items | 0.10 ms |
| cleaning up | 0.05 ms |
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 14 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/tables/categoryacl.php:79 |
| 13 | EasyBlogTableCategoryAcl->getUserAssignedCategoryACL() | JROOT/administrator/components/com_easyblog/includes/category/category.php:287 |
| 12 | EasyBlogCategory::genCatAccessSQL() | JROOT/administrator/components/com_easyblog/models/categories.php:775 |
| 11 | EasyBlogModelCategories->getChildCategories() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:2261 |
| 10 | EB::buildNestedCategories() | JROOT/components/com_easyblog/views/categories/view.html.php:209 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.99 ms After last query: 0.07 ms Query memory: 0.022 MB Memory before query: 25.704 MB Rows returned: 0
select a.`id`, a.`title`, a.`alias`, a.`private`, a.`parent_id`, a.`avatar`, a.`description`
from `l6r3h_easyblog_category` as a
WHERE a.`lft` > '17'
AND a.`lft` < '18'
and a.`published` = '1'
AND (( (a.`private` = 0) OR (a.`private` = 1
AND '0' > 0) OR (a.`private` = 2
AND ( SELECT COUNT(1)
FROM `l6r3h_easyblog_category_acl` as ca
WHERE ca.`category_id` = a.`id`
AND ca.`acl_id` = '1'
AND ( (ca.`content_id` IN ('11')
AND ca.`type` = '
group') OR (ca.`content_id` = '0'
AND ca.`type` = 'user') ) ) > 0 ) ))
ORDER BY a.`lft` ASC
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | PRIMARY | a | NULL | range | easyblog_cat_published,easyblog_cat_private,easyblog_cat_lft,idx_category_access,idx_cat_lftrgt | easyblog_cat_lft | 5 | NULL | 1 | 100.00 | Using index condition; Using where |
| 2 | DEPENDENT SUBQUERY | ca | NULL | ref | easyblog_category_acl,easyblog_category_acl_id,easyblog_content_type,easyblog_category_content_type,idx_cat_post_acl | easyblog_category_acl | 8 | db597855425.a.id | 1 | 100.00 | Using index condition; Using where |
| Status | Duration |
|---|
| starting | 0.22 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.03 ms |
| init | 0.10 ms |
| System lock | 0.02 ms |
| optimizing | 0.04 ms |
| statistics | 0.15 ms |
| preparing | 0.04 ms |
| Sorting result | 0.01 ms |
| optimizing | 0.03 ms |
| statistics | 0.09 ms |
| preparing | 0.03 ms |
| executing | 0.01 ms |
| Sending data | 0.06 ms |
| end | 0.01 ms |
| query end | 0.02 ms |
| closing tables | 0.02 ms |
| freeing items | 0.10 ms |
| cleaning up | 0.04 ms |
| # | Caller | File and line number |
|---|
| 14 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 13 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 12 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/categories.php:815 |
| 11 | EasyBlogModelCategories->getChildCategories() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:2261 |
| 10 | EB::buildNestedCategories() | JROOT/components/com_easyblog/views/categories/view.html.php:209 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 4.63 ms After last query: 1.72 ms Query memory: 0.022 MB Memory before query: 25.920 MB Rows returned: 1
SELECT COUNT(1) AS `cnt`
FROM `l6r3h_easyblog_post_category` AS `a`
INNER JOIN `l6r3h_easyblog_post` AS `b`
ON a.`post_id` = b.`id`
AND b.`published`='1'
INNER JOIN `l6r3h_easyblog_category` AS `c`
ON a.`category_id` = c.`id`
INNER JOIN `l6r3h_users` AS `uu`
ON b.`created_by` = uu.`id`
AND b.`access` = '0'
WHERE (c.`id` IN (9) or c.`parent_id` IN (9))
AND b.`state`='0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | b | NULL | ref | PRIMARY,easyblog_post_published,easyblog_post_created_by,easyblog_post_blogger_list,easyblog_post_search,easyblog_frontpage1,easyblog_post_searchnew,idx_pre_soucetype_postcount,idx_post_sql1,idx_latest_posts | idx_pre_soucetype_postcount | 5 | const,const | 231 | 10.00 | Using where |
| 1 | SIMPLE | uu | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.b.created_by | 1 | 100.00 | Using where; Using index |
| 1 | SIMPLE | a | NULL | ref | eb_post_category_postid,eb_post_category_catid,eb_post_category_post_cat,eb_post_category_cat_post | eb_post_category_post_cat | 4 | db597855425.b.id | 1 | 100.00 | Using where; Using index |
| 1 | SIMPLE | c | NULL | eq_ref | PRIMARY,easyblog_cat_parentid | PRIMARY | 8 | db597855425.a.category_id | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.15 ms |
| checking permissions | 0.02 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 1.98 ms |
| init | 0.05 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.17 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 1.23 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1550 |
| 12 | JDatabaseDriver->loadColumn() | JROOT/administrator/components/com_easyblog/includes/utils.php:184 |
| 11 | EasyBlogDbJoomla->loadResultArray() | JROOT/administrator/components/com_easyblog/models/category.php:663 |
| 10 | EasyBlogModelCategory->getTotalPostCount() | JROOT/components/com_easyblog/views/categories/view.html.php:249 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 6.11 ms After last query: 1.17 ms Query memory: 0.022 MB Memory before query: 26.120 MB Rows returned: 1
SELECT COUNT(1)
FROM `l6r3h_easyblog_post` AS a
LEFT JOIN `l6r3h_easyblog_featured` as f
ON a.`id` = f.`content_id`
AND f.`type` = 'post'
INNER JOIN `l6r3h_users` AS uu
ON a.`created_by` = uu.`id`
and uu.`block` = 0
WHERE a.`published`='1'
AND a.`state`='0'
AND ((a.`source_type` = 'easyblog.sitewide') OR ( a.`source_type` = 'easyblog.team'
and 1 <= (select count(1)
from `l6r3h_easyblog_team` as srcteam
where srcteam.`id` = a.`source_id`
and srcteam.`published` = 1
and ( (srcteam.`access` = 3) OR (srcteam.`access` = 2
and (select count(1)
from `l6r3h_easyblog_team_groups` as srcteamgrp
where srcteamgrp.`team_id` = srcteam.`id`
and srcteamgrp.`group_id` IN (11) ) > 0)))))
AND (1 <= (select count(1)
from `l6r3h_easyblog_post_category` AS acp
INNER JOIN `l6r3h_easyblog_category` as cat
on acp.`category_id` = cat.`id`
where acp.`post_id` = a.`id`
AND cat.`id` = 9
and ( ( cat.`private` = 0 ) OR ( (cat.`private` = 1)
and (0 > 0) ) OR ( (cat.`private` = 2)
and ( (select count(1)
from `l6r3h_easyblog_category_acl` as cacl
where cacl.`category_id` = cat.id
and cacl.`acl_id` = 1
and cacl.`content_id` in (11)) > 0 ) ) )
and not exists ( select acp2.post_id
from `l6r3h_easyblog_post_category` as acp2
inner join `l6r3h_easyblog_category` as cat2
on acp2.`category_id` = cat2.`id`
where acp2.`post_id` = acp.`post_id`
and ( ( cat2.`private` = 1
and (0 = 0) ) OR ( cat2.`private` = 2
and (select count(1)
from `l6r3h_easyblog_category_acl` as cacl2
where cacl2.`category_id` = cat2.`id`
and cacl2.`acl_id` = 1
and cacl2.`content_id` IN (11)) = 0 ) ) ) ))
AND a.`access` = '0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | PRIMARY | a | NULL | ref | easyblog_post_published,easyblog_post_created_by,easyblog_post_blogger_list,easyblog_post_search,easyblog_frontpage1,easyblog_post_searchnew,idx_pre_soucetype_postcount,idx_post_sql1,idx_latest_posts | idx_latest_posts | 9 | const,const,const | 231 | 19.00 | Using where |
| 1 | PRIMARY | f | NULL | ref | easyblog_featured_content_type,easyblog_content | easyblog_featured_content_type | 775 | db597855425.a.id,const | 1 | 100.00 | Using index |
| 1 | PRIMARY | uu | NULL | eq_ref | PRIMARY,idx_block | PRIMARY | 4 | db597855425.a.created_by | 1 | 58.76 | Using where |
| 4 | DEPENDENT SUBQUERY | cat | NULL | const | PRIMARY,easyblog_cat_private | PRIMARY | 8 | const | 1 | 100.00 | NULL |
| 4 | DEPENDENT SUBQUERY | acp | NULL | ref | eb_post_category_postid,eb_post_category_catid,eb_post_category_post_cat,eb_post_category_cat_post | eb_post_category_post_cat | 8 | db597855425.a.id,const | 1 | 100.00 | Using where; Using index |
| 6 | DEPENDENT SUBQUERY | acp2 | NULL | ref | eb_post_category_postid,eb_post_category_catid,eb_post_category_post_cat,eb_post_category_cat_post | eb_post_category_post_cat | 4 | db597855425.acp.post_id | 1 | 100.00 | Using index |
| 6 | DEPENDENT SUBQUERY | cat2 | NULL | eq_ref | PRIMARY,easyblog_cat_private | PRIMARY | 8 | db597855425.acp2.category_id | 1 | 20.00 | Using where |
| 7 | DEPENDENT SUBQUERY | cacl2 | NULL | ref | easyblog_category_acl,easyblog_category_acl_id,easyblog_content_type,easyblog_category_content_type,idx_cat_post_acl | easyblog_category_acl | 8 | db597855425.cat2.id | 1 | 100.00 | Using index condition; Using where |
| 5 | DEPENDENT SUBQUERY | cacl | NULL | ref | easyblog_category_acl,easyblog_category_acl_id,easyblog_content_type,easyblog_category_content_type,idx_cat_post_acl | easyblog_category_acl | 8 | const | 1 | 100.00 | Using index condition; Using where |
| 2 | DEPENDENT SUBQUERY | srcteam | NULL | eq_ref | PRIMARY,idx_viewable_team,idx_published,idx_access | PRIMARY | 4 | db597855425.a.source_id | 1 | 100.00 | Using where |
| 3 | DEPENDENT SUBQUERY | srcteamgrp | NULL | ref | team_id,group_id,idx_team_group | team_id | 4 | db597855425.srcteam.id | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| Sending data | 0.03 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.03 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.02 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.02 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.03 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.02 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.02 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 12 | JDatabaseDriver->loadResult() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 11 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/category.php:1553 |
| 10 | EasyBlogModelCategory->getPosts() | JROOT/components/com_easyblog/views/categories/view.html.php:336 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 8.17 ms After last query: 1.17 ms Query memory: 0.131 MB Memory before query: 26.231 MB Rows returned: 10
SELECT a.*, ifnull(f.`id`, 0) as `featured`
FROM `l6r3h_easyblog_post` AS a
LEFT JOIN `l6r3h_easyblog_featured` as f
ON a.`id` = f.`content_id`
AND f.`type` = 'post'
INNER JOIN `l6r3h_users` AS uu
ON a.`created_by` = uu.`id`
and uu.`block` = 0
WHERE a.`published`='1'
AND a.`state`='0'
AND ((a.`source_type` = 'easyblog.sitewide') OR ( a.`source_type` = 'easyblog.team'
and 1 <= (select count(1)
from `l6r3h_easyblog_team` as srcteam
where srcteam.`id` = a.`source_id`
and srcteam.`published` = 1
and ( (srcteam.`access` = 3) OR (srcteam.`access` = 2
and (select count(1)
from `l6r3h_easyblog_team_groups` as srcteamgrp
where srcteamgrp.`team_id` = srcteam.`id`
and srcteamgrp.`group_id` IN (11) ) > 0)))))
AND (1 <= (select count(1)
from `l6r3h_easyblog_post_category` AS acp
INNER JOIN `l6r3h_easyblog_category` as cat
on acp.`category_id` = cat.`id`
where acp.`post_id` = a.`id`
AND cat.`id` = 9
and ( ( cat.`private` = 0 ) OR ( (cat.`private` = 1)
and (0 > 0) ) OR ( (cat.`private` = 2)
and ( (select count(1)
from `l6r3h_easyblog_category_acl` as cacl
where cacl.`category_id` = cat.id
and cacl.`acl_id` = 1
and cacl.`content_id` in (11)) > 0 ) ) )
and not exists ( select acp2.post_id
from `l6r3h_easyblog_post_category` as acp2
inner join `l6r3h_easyblog_category` as cat2
on acp2.`category_id` = cat2.`id`
where acp2.`post_id` = acp.`post_id`
and ( ( cat2.`private` = 1
and (0 = 0) ) OR ( cat2.`private` = 2
and (select count(1)
from `l6r3h_easyblog_category_acl` as cacl2
where cacl2.`category_id` = cat2.`id`
and cacl2.`acl_id` = 1
and cacl2.`content_id` IN (11)) = 0 ) ) ) ))
AND a.`access` = '0'
ORDER BY a.`created` DESC
LIMIT 40,10
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | PRIMARY | a | NULL | ref | easyblog_post_published,easyblog_post_created_by,easyblog_post_blogger_list,easyblog_post_search,easyblog_frontpage1,easyblog_post_searchnew,idx_pre_soucetype_postcount,idx_post_sql1,idx_latest_posts | idx_latest_posts | 9 | const,const,const | 231 | 19.00 | Using index condition; Using where; Using filesort |
| 1 | PRIMARY | f | NULL | ref | easyblog_featured_content_type,easyblog_content | easyblog_featured_content_type | 775 | db597855425.a.id,const | 1 | 100.00 | Using index |
| 1 | PRIMARY | uu | NULL | eq_ref | PRIMARY,idx_block | PRIMARY | 4 | db597855425.a.created_by | 1 | 58.76 | Using where |
| 4 | DEPENDENT SUBQUERY | cat | NULL | const | PRIMARY,easyblog_cat_private | PRIMARY | 8 | const | 1 | 100.00 | NULL |
| 4 | DEPENDENT SUBQUERY | acp | NULL | ref | eb_post_category_postid,eb_post_category_catid,eb_post_category_post_cat,eb_post_category_cat_post | eb_post_category_post_cat | 8 | db597855425.a.id,const | 1 | 100.00 | Using where; Using index |
| 6 | DEPENDENT SUBQUERY | acp2 | NULL | ref | eb_post_category_postid,eb_post_category_catid,eb_post_category_post_cat,eb_post_category_cat_post | eb_post_category_post_cat | 4 | db597855425.acp.post_id | 1 | 100.00 | Using index |
| 6 | DEPENDENT SUBQUERY | cat2 | NULL | eq_ref | PRIMARY,easyblog_cat_private | PRIMARY | 8 | db597855425.acp2.category_id | 1 | 20.00 | Using where |
| 7 | DEPENDENT SUBQUERY | cacl2 | NULL | ref | easyblog_category_acl,easyblog_category_acl_id,easyblog_content_type,easyblog_category_content_type,idx_cat_post_acl | easyblog_category_acl | 8 | db597855425.cat2.id | 1 | 100.00 | Using index condition; Using where |
| 5 | DEPENDENT SUBQUERY | cacl | NULL | ref | easyblog_category_acl,easyblog_category_acl_id,easyblog_content_type,easyblog_category_content_type,idx_cat_post_acl | easyblog_category_acl | 8 | const | 1 | 100.00 | Using index condition; Using where |
| 2 | DEPENDENT SUBQUERY | srcteam | NULL | eq_ref | PRIMARY,idx_viewable_team,idx_published,idx_access | PRIMARY | 4 | db597855425.a.source_id | 1 | 100.00 | Using where |
| 3 | DEPENDENT SUBQUERY | srcteamgrp | NULL | ref | team_id,group_id,idx_team_group | team_id | 4 | db597855425.srcteam.id | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.02 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.03 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.02 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.02 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.02 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.45 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.02 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 12 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 11 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/category.php:1576 |
| 10 | EasyBlogModelCategory->getPosts() | JROOT/components/com_easyblog/views/categories/view.html.php:336 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.01 ms After last query: 0.16 ms Query memory: 0.022 MB Memory before query: 26.325 MB Rows returned: 1
SELECT COUNT(1)
FROM `l6r3h_easyblog_category_acl`
WHERE `acl_id` = '1'
AND `status` = '1'
AND `category_id` = '9'
AND `content_id` IN ('11')
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_category_acl | NULL | ref | easyblog_category_acl,easyblog_category_acl_id,easyblog_content_type,easyblog_category_content_type,idx_cat_post_acl | easyblog_category_acl | 8 | const | 1 | 100.00 | Using index condition; Using where |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.05 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 12 | JDatabaseDriver->loadResult() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 11 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/category.php:1953 |
| 10 | EasyBlogModelCategory->allowAclCategory() | JROOT/components/com_easyblog/views/categories/view.html.php:342 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.77 ms After last query: 1.65 ms Query memory: 0.024 MB Memory before query: 26.502 MB Rows returned: 0
SELECT COUNT(1) as `voted`, `uid`
FROM `l6r3h_easyblog_ratings`
WHERE `uid` IN (131,129,128,127,126,125,123,122,107,106)
AND `type`='entry'
AND `created_by`='0'
AND (`sessionid` = '51dbc64054b6cd26e11d097e812a4484' OR `ip` = '3.138.138.144')
GROUP BY `uid`
ORDER BY NULL
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_ratings | NULL | ref | post_id,created_by,idx_uid_type,idx_uid_type_user,idx_uid_type_user_session,idx_uid_type_user_ipaddr | created_by | 4 | const | 1 | 100.00 | Using index condition; Using where; Using temporary |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.23 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.14 ms |
| preparing | 0.02 ms |
| Creating tmp table | 0.03 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| removing tmp table | 0.01 ms |
| query end | 0.00 ms |
| closing tables | 0.02 ms |
| freeing items | 0.16 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 17 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 16 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/ratings.php:135 |
| 15 | EasyBlogModelRatings->preloadUserPostRatings() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:452 |
| 14 | EasyBlogCache->cacheVoted() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:357 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.21 ms After last query: 0.08 ms Query memory: 0.024 MB Memory before query: 26.511 MB Rows returned: 0
SELECT AVG(`value`) AS `ratings` ,COUNT(1) AS `total` ,`uid`
FROM `l6r3h_easyblog_ratings` AS a
WHERE a.`uid` IN(131,129,128,127,126,125,123,122,107,106)
AND `type`='entry'
GROUP BY `uid`
ORDER BY NULL
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | a | NULL | index | post_id,idx_uid_type,idx_uid_type_user,idx_uid_type_user_ipaddr | idx_uid_type | 775 | NULL | 1 | 100.00 | Using where; Using index |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.02 ms |
| optimizing | 0.01 ms |
| statistics | 0.12 ms |
| preparing | 0.02 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 17 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 16 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/ratings.php:176 |
| 15 | EasyBlogModelRatings->preloadRatings() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:583 |
| 14 | EasyBlogCache->cacheRatings() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:362 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.40 ms After last query: 1.40 ms Query memory: 0.024 MB Memory before query: 26.693 MB Rows returned: 0
SELECT a.`post_id`, COUNT(1) AS `count`
FROM `l6r3h_easyblog_comment` AS a
LEFT JOIN `l6r3h_users` AS uu
ON a.`created_by` = uu.`id`
WHERE a.`post_id` IN(131,129,128,127,126,125,123,122,107,106)
AND a.`published`='1'
AND (uu.`block` = 0 OR uu.`id` IS NULL)
GROUP BY a.`post_id`
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | a | NULL | ALL | easyblog_comment_postid,idx_comment_post_items | NO INDEX KEY COULD BE USED | NULL | NULL | 38 | 2.63 | Using where; Using temporary; Using filesort |
| 1 | SIMPLE | uu | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.a.created_by | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.17 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.07 ms |
| preparing | 0.03 ms |
| Creating tmp table | 0.02 ms |
| Sorting result | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.04 ms |
| Creating sort index | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| removing tmp table | 0.01 ms |
| query end | 0.00 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 17 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 16 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/comment.php:627 |
| 15 | EasyBlogModelComment->preloadCommentCount() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:641 |
| 14 | EasyBlogCache->cacheCommentCount() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:372 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.59 ms After last query: 0.11 ms Query memory: 0.028 MB Memory before query: 26.702 MB Rows returned: 10
select a.*, b.`post_id`, b.`primary`
from `l6r3h_easyblog_category` as a
inner join `l6r3h_easyblog_post_category` as b
on a.`id` = b.`category_id`
where b.`post_id` IN (131,129,128,127,126,125,123,122,107,106)
order by a.`lft` asc
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | b | NULL | range | eb_post_category_postid,eb_post_category_catid,eb_post_category_post_cat,eb_post_category_cat_post | eb_post_category_postid | 4 | NULL | 10 | 100.00 | Using index condition; Using temporary; Using filesort |
| 1 | SIMPLE | a | NULL | eq_ref | PRIMARY | PRIMARY | 8 | db597855425.b.category_id | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.07 ms |
| preparing | 0.01 ms |
| Creating tmp table | 0.03 ms |
| Sorting result | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.31 ms |
| Creating sort index | 0.06 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| removing tmp table | 0.07 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 17 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 16 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/category.php:1977 |
| 15 | EasyBlogModelCategory->preloadByPosts() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:728 |
| 14 | EasyBlogCache->cacheCategories() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:377 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.51 ms After last query: 1.84 ms Query memory: 0.028 MB Memory before query: 26.871 MB Rows returned: 18
select a.*, b.`post_id`
from `l6r3h_easyblog_tag` as a
inner join `l6r3h_easyblog_post_tag` as b
on a.`id` = b.`tag_id`
where b.`post_id` IN (131,129,128,127,126,125,123,122,107,106)
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | b | NULL | range | easyblog_post_tag_tag_id,easyblog_post_tag_post_id,easyblog_post_tagpost_id | easyblog_post_tag_post_id | 8 | NULL | 21 | 100.00 | Using index condition |
| 1 | SIMPLE | a | NULL | eq_ref | PRIMARY | PRIMARY | 8 | db597855425.b.tag_id | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.24 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.06 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.11 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 17 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 16 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/tags.php:929 |
| 15 | EasyBlogModelTags->preloadByPosts() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:810 |
| 14 | EasyBlogCache->cacheTags() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:382 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.25 ms After last query: 4.17 ms Query memory: 0.057 MB Memory before query: 27.191 MB Rows returned: 10
select a.*
from `l6r3h_easyblog_revisions` as a
where a.`id` IN ( 79,192,193,58,194,78,77,177,210,108)
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | a | NULL | range | PRIMARY | PRIMARY | 8 | NULL | 10 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.02 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.11 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.02 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 17 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 16 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/revisions.php:624 |
| 15 | EasyBlogModelRevisions->preload() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:704 |
| 14 | EasyBlogCache->cacheRevisions() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:387 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.32 ms After last query: 3.27 ms Query memory: 0.026 MB Memory before query: 28.603 MB Rows returned: 1
select u.*, e.`id` as `eb_id`, e.`nickname`, e.`avatar`, e.`description`, e.`url`, e.`params` as `eb_params`, e.`published` as `eb_published`, e.`title` as `eb_title`, e.`biography`, e.`permalink`, e.`custom_css`, e.`ordering`
from `l6r3h_users` as u
left join `l6r3h_easyblog_users` as e
ON u.`id` = e.`id`
where u.`id` = 43
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | u | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| 1 | SIMPLE | e | NULL | const | PRIMARY | PRIMARY | 8 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.16 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 21 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 20 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 19 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/users.php:298 |
| 18 | EasyBlogModelUsers->getUsersMeta() | JROOT/administrator/components/com_easyblog/includes/user/user.php:139 |
| 17 | EasyBlogUser::loadUsers() | JROOT/administrator/components/com_easyblog/includes/user/user.php:36 |
| 16 | EasyBlogUser::factory() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1084 |
| 15 | EB::user() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:791 |
| 14 | EasyBlogCache->cacheAuthors() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:392 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.68 ms After last query: 1.24 ms Query memory: 0.031 MB Memory before query: 28.690 MB Rows returned: 17
SHOW FULL COLUMNS
FROM `l6r3h_users`
EXPLAIN not possible on query: SHOW FULL COLUMNS FROM `l6r3h_users`
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.20 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Opening tables | 0.01 ms |
| checking permissions | 0.03 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.00 ms |
| removing tmp table | 0.07 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 29 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 28 | JDatabaseDriver->loadObjectList() | JROOT/libraries/joomla/database/driver/mysqli.php:448 |
| 27 | JDatabaseDriverMysqli->getTableColumns() | JROOT/libraries/src/Table/Table.php:261 |
| 26 | Joomla\CMS\Table\Table->getFields() | JROOT/libraries/src/Table/Table.php:180 |
| 25 | Joomla\CMS\Table\Table->__construct() | JROOT/libraries/src/Table/User.php:41 |
| 24 | Joomla\CMS\Table\User->__construct() | JROOT/libraries/src/Table/Table.php:328 |
| 23 | Joomla\CMS\Table\Table::getInstance() | JROOT/libraries/src/User/User.php:603 |
| 22 | Joomla\CMS\User\User::getTable() | JROOT/libraries/src/User/User.php:877 |
| 21 | Joomla\CMS\User\User->load() | JROOT/libraries/src/User/User.php:248 |
| 20 | Joomla\CMS\User\User->__construct() | JROOT/libraries/src/User/User.php:301 |
| 19 | Joomla\CMS\User\User::getInstance() | JROOT/libraries/src/Factory.php:266 |
| 18 | Joomla\CMS\Factory::getUser() | JROOT/administrator/components/com_easyblog/includes/user/user.php:186 |
| 17 | EasyBlogUser::loadUsers() | JROOT/administrator/components/com_easyblog/includes/user/user.php:36 |
| 16 | EasyBlogUser::factory() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1084 |
| 15 | EB::user() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:791 |
| 14 | EasyBlogCache->cacheAuthors() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:392 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.35 ms After last query: 0.11 ms Query memory: 0.027 MB Memory before query: 28.722 MB Rows returned: 1
SELECT *
FROM `l6r3h_users`
WHERE `id` = 43
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_users | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.03 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 24 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1465 |
| 23 | JDatabaseDriver->loadAssoc() | JROOT/libraries/src/Table/User.php:87 |
| 22 | Joomla\CMS\Table\User->load() | JROOT/libraries/src/User/User.php:880 |
| 21 | Joomla\CMS\User\User->load() | JROOT/libraries/src/User/User.php:248 |
| 20 | Joomla\CMS\User\User->__construct() | JROOT/libraries/src/User/User.php:301 |
| 19 | Joomla\CMS\User\User::getInstance() | JROOT/libraries/src/Factory.php:266 |
| 18 | Joomla\CMS\Factory::getUser() | JROOT/administrator/components/com_easyblog/includes/user/user.php:186 |
| 17 | EasyBlogUser::loadUsers() | JROOT/administrator/components/com_easyblog/includes/user/user.php:36 |
| 16 | EasyBlogUser::factory() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1084 |
| 15 | EB::user() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:791 |
| 14 | EasyBlogCache->cacheAuthors() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:392 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.50 ms After last query: 2.75 ms Query memory: 0.027 MB Memory before query: 29.486 MB Rows returned: 4
SELECT `g`.`id`,`g`.`title`
FROM `l6r3h_usergroups` AS g
INNER JOIN `l6r3h_user_usergroup_map` AS m
ON m.group_id = g.id
WHERE `m`.`user_id` = 43
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | m | NULL | ref | PRIMARY | PRIMARY | 4 | const | 4 | 100.00 | Using index |
| 1 | SIMPLE | g | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.m.group_id | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.07 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.05 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.06 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.27 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 24 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1506 |
| 23 | JDatabaseDriver->loadAssocList() | JROOT/libraries/src/Table/User.php:112 |
| 22 | Joomla\CMS\Table\User->load() | JROOT/libraries/src/User/User.php:880 |
| 21 | Joomla\CMS\User\User->load() | JROOT/libraries/src/User/User.php:248 |
| 20 | Joomla\CMS\User\User->__construct() | JROOT/libraries/src/User/User.php:301 |
| 19 | Joomla\CMS\User\User::getInstance() | JROOT/libraries/src/Factory.php:266 |
| 18 | Joomla\CMS\Factory::getUser() | JROOT/administrator/components/com_easyblog/includes/user/user.php:186 |
| 17 | EasyBlogUser::loadUsers() | JROOT/administrator/components/com_easyblog/includes/user/user.php:36 |
| 16 | EasyBlogUser::factory() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1084 |
| 15 | EB::user() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:791 |
| 14 | EasyBlogCache->cacheAuthors() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:392 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.62 ms After last query: 0.25 ms Query memory: 0.024 MB Memory before query: 29.499 MB Rows returned: 0
select `a`.`id` as `cat_fg_id`, `a`.`category_id` as `cat_fg_category_id`, `a`.`group_id` as `cat_fg_group_id`, `fg`.`id` as `fg_id`, `fg`.`title` as `fg_title`, `fg`.`description` as `fg_description`, `fg`.`created` as `fg_created`, `fg`.`state` as `fg_state`, `fg`.`read` as `fg_read`, `fg`.`write` as `fg_write`, `fg`.`params` as `fg_params`, `f`.`id` as `f_id`, `f`.`group_id` as `f_group_id`, `f`.`title` as `f_title`, `f`.`help` as `f_help`, `f`.`state` as `f_state`, `f`.`required` as `f_required`, `f`.`type` as `f_type`, `f`.`params` as `f_params`, `f`.`created` as `f_created`, `f`.`options` as `f_options`, `f`.`ordering` as `f_ordering`,`fv`.`id` as `fv_id`, `fv`.`field_id` as `fv_field_id`, `fv`.`post_id` as `fv_post_id`, `fv`.`value` as `fv_value`
from `l6r3h_easyblog_category_fields_groups` as a
inner join `l6r3h_easyblog_post_category` as p
on `a`.`category_id` = `p`.`category_id`
inner join `l6r3h_easyblog_fields_groups` as fg
on `a`.`group_id` = `fg`.`id`
inner join `l6r3h_easyblog_fields` as f
on `fg`.`id` = `f`.`group_id`
left join `l6r3h_easyblog_fields_values` as fv
on `fv`.`field_id` = `f`.`id`
and `fv`.`post_id` = `p`.`post_id`
LEFT JOIN `l6r3h_easyblog_fields_groups_acl` AS acl
ON fg.`id` = acl.`group_id`
where p.post_id IN (131,129,128,127,126,125,123,122,107,106)
AND ( acl.`acl_id` IN(11)
AND acl.`acl_type` = 'read' OR acl.`id` IS NULL )
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | a | NULL | index | category_id,cat_id | category_id | 8 | NULL | 1 | 100.00 | Using index |
| 1 | SIMPLE | fg | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.a.group_id | 1 | 100.00 | NULL |
| 1 | SIMPLE | f | NULL | ref | group_id,idx_group_ordering | group_id | 4 | db597855425.a.group_id | 1 | 100.00 | NULL |
| 1 | SIMPLE | p | NULL | range | eb_post_category_postid,eb_post_category_catid,eb_post_category_post_cat,eb_post_category_cat_post | eb_post_category_post_cat | 4 | NULL | 10 | 11.11 | Using where; Using index; Using join buffer (Block Nested Loop) |
| 1 | SIMPLE | fv | NULL | ref | field_id,post_id | field_id | 4 | db597855425.f.id | 1 | 100.00 | Using where |
| 1 | SIMPLE | acl | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 1 | 100.00 | Using where; Using join buffer (Block Nested Loop) |
| Status | Duration |
|---|
| starting | 0.14 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.69 ms |
| init | 0.07 ms |
| System lock | 0.01 ms |
| optimizing | 0.03 ms |
| statistics | 0.20 ms |
| preparing | 0.23 ms |
| executing | 0.02 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.02 ms |
| closing tables | 0.04 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 17 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 16 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/fields.php:305 |
| 15 | EasyBlogModelFields->preloadFields() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:489 |
| 14 | EasyBlogCache->cacheFields() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:397 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.52 ms After last query: 0.55 ms Query memory: 0.026 MB Memory before query: 29.559 MB Rows returned: 10
select *
from `l6r3h_easyblog_meta`
where `content_id` in (131,129,128,127,126,125,123,122,107,106)
and `type` = 'post'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_meta | NULL | range | idx_meta_content_type | idx_meta_content_type | 66 | NULL | 10 | 100.00 | Using index condition |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.18 ms |
| init | 0.03 ms |
| System lock | 0.03 ms |
| optimizing | 0.01 ms |
| statistics | 0.08 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.10 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 17 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 16 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/metas.php:386 |
| 15 | EasyBlogModelMetas->preloadPostMetas() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:418 |
| 14 | EasyBlogCache->cacheMetas() | JROOT/administrator/components/com_easyblog/includes/cache/cache.php:402 |
| 13 | EasyBlogCache->insert() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:29 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.55 ms After last query: 6.66 ms Query memory: 0.024 MB Memory before query: 30.286 MB Rows returned: 0
SELECT a.`id`, a.`title`, a.`alias`
FROM `l6r3h_easyblog_tag` AS a
LEFT JOIN `l6r3h_easyblog_post_tag` AS b
ON a.`id`= b.`tag_id`
WHERE b.`post_id`='125'
AND b.`isrevision` IS NULL
AND a.`published`='1'
ORDER BY b.`id` ASC
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | b | NULL | ref | easyblog_post_tag_tag_id,easyblog_post_tag_post_id,easyblog_post_tagpost_id | easyblog_post_tag_post_id | 8 | const | 1 | 10.00 | Using index condition; Using where |
| 1 | SIMPLE | a | NULL | eq_ref | PRIMARY,easyblog_tag_published,easyblog_tag_query1 | PRIMARY | 8 | db597855425.b.tag_id | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.14 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.03 ms |
| init | 0.04 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.12 ms |
| preparing | 0.04 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.06 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 17 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 16 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 15 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/posttag.php:59 |
| 14 | EasyBlogModelPostTag->getBlogTags() | JROOT/administrator/components/com_easyblog/includes/post/post.php:7790 |
| 13 | EasyBlogPost->getTags() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:107 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 3.97 ms After last query: 0.47 ms Query memory: 0.024 MB Memory before query: 30.347 MB Rows returned: 0
SELECT a.`id`, a.`title`, a.`alias`
FROM `l6r3h_easyblog_tag` AS a
LEFT JOIN `l6r3h_easyblog_post_tag` AS b
ON a.`id`= b.`tag_id`
WHERE b.`post_id`='122'
AND b.`isrevision` IS NULL
AND a.`published`='1'
ORDER BY b.`id` ASC
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | b | NULL | ref | easyblog_post_tag_tag_id,easyblog_post_tag_post_id,easyblog_post_tagpost_id | easyblog_post_tag_post_id | 8 | const | 1 | 10.00 | Using index condition; Using where |
| 1 | SIMPLE | a | NULL | eq_ref | PRIMARY,easyblog_tag_published,easyblog_tag_query1 | PRIMARY | 8 | db597855425.b.tag_id | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.09 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 2.54 ms |
| statistics | 0.08 ms |
| preparing | 0.03 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 17 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 16 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 15 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/posttag.php:59 |
| 14 | EasyBlogModelPostTag->getBlogTags() | JROOT/administrator/components/com_easyblog/includes/post/post.php:7790 |
| 13 | EasyBlogPost->getTags() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:107 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.13 ms After last query: 0.22 ms Query memory: 0.024 MB Memory before query: 30.373 MB Rows returned: 0
SELECT a.`id`, a.`title`, a.`alias`
FROM `l6r3h_easyblog_tag` AS a
LEFT JOIN `l6r3h_easyblog_post_tag` AS b
ON a.`id`= b.`tag_id`
WHERE b.`post_id`='107'
AND b.`isrevision` IS NULL
AND a.`published`='1'
ORDER BY b.`id` ASC
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | b | NULL | ref | easyblog_post_tag_tag_id,easyblog_post_tag_post_id,easyblog_post_tagpost_id | easyblog_post_tag_post_id | 8 | const | 1 | 10.00 | Using index condition; Using where |
| 1 | SIMPLE | a | NULL | eq_ref | PRIMARY,easyblog_tag_published,easyblog_tag_query1 | PRIMARY | 8 | db597855425.b.tag_id | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.07 ms |
| preparing | 0.02 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 17 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 16 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 15 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/posttag.php:59 |
| 14 | EasyBlogModelPostTag->getBlogTags() | JROOT/administrator/components/com_easyblog/includes/post/post.php:7790 |
| 13 | EasyBlogPost->getTags() | JROOT/administrator/components/com_easyblog/includes/formatter/types/list.php:107 |
| 12 | EasyBlogFormatterList->execute() | JROOT/administrator/components/com_easyblog/includes/formatter/formatter.php:55 |
| 11 | EasyBlogFormatter->execute() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:3463 |
| 10 | EB::formatter() | JROOT/components/com_easyblog/views/categories/view.html.php:382 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.80 ms After last query: 0.21 ms Query memory: 0.022 MB Memory before query: 30.395 MB Rows returned: 0
SELECT `id`
FROM `l6r3h_easyblog_subscriptions`
WHERE `uid` = '9'
AND `utype` = 'category'
AND `email` = ''
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_subscriptions | NULL | ref | easyblog_subscriptions_types,easyblog_subscriptions_types_userid,easyblog_subscriptions_types_email,easyblog_subscriptions_email | easyblog_subscriptions_types | 202 | const,const | 1 | 100.00 | Using index condition; Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.26 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.07 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.39 ms |
| end | 0.02 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 12 | JDatabaseDriver->loadResult() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 11 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/models/category.php:1842 |
| 10 | EasyBlogModelCategory->isCategorySubscribedEmail() | JROOT/components/com_easyblog/views/categories/view.html.php:386 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.19 ms After last query: 0.15 ms Query memory: 0.022 MB Memory before query: 30.406 MB Rows returned: 1
SELECT *
FROM l6r3h_easyblog_meta
WHERE `content_id` = '9'
AND `type` = 'category'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_meta | NULL | ref | idx_meta_content_type | idx_meta_content_type | 66 | const,const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.12 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.05 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1465 |
| 12 | JDatabaseDriver->loadAssoc() | JROOT/libraries/src/Table/Table.php:747 |
| 11 | Joomla\CMS\Table\Table->load() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1718 |
| 10 | EB::setMeta() | JROOT/components/com_easyblog/views/categories/view.html.php:406 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.40 ms After last query: 20.74 ms Query memory: 0.132 MB Memory before query: 31.838 MB Rows returned: 70
SELECT m.id, m.title, m.module, m.position, m.content, m.showtitle, m.params, mm.menuid
FROM l6r3h_modules AS m
LEFT JOIN l6r3h_modules_menu AS mm
ON mm.moduleid = m.id
LEFT JOIN l6r3h_extensions AS e
ON e.element = m.module
AND e.client_id = m.client_id
WHERE m.published = 1
AND e.enabled = 1
AND (m.publish_up = '0000-00-00 00:00:00' OR m.publish_up <= '2024-04-16 08:16:26')
AND (m.publish_down = '0000-00-00 00:00:00' OR m.publish_down >= '2024-04-16 08:16:26')
AND m.access IN (1,1,6)
AND m.client_id = 0
AND (mm.menuid = 486 OR mm.menuid <= 0)
ORDER BY m.position, m.ordering
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | m | NULL | ref | PRIMARY,published,newsfeeds | published | 1 | const | 25 | 1.96 | Using index condition; Using where; Using filesort |
| 1 | SIMPLE | e | NULL | ref | element_clientid,element_folder_clientid | element_clientid | 403 | db597855425.m.module,const | 1 | 10.00 | Using index condition; Using where |
| 1 | SIMPLE | mm | NULL | ref | PRIMARY | PRIMARY | 4 | db597855425.m.id | 2 | 40.00 | Using where; Using index |
| Status | Duration |
|---|
| starting | 0.10 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.14 ms |
| init | 0.06 ms |
| System lock | 0.01 ms |
| optimizing | 0.03 ms |
| statistics | 0.09 ms |
| preparing | 0.03 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.02 ms |
| Creating sort index | 0.72 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 20 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 19 | JDatabaseDriver->loadObjectList() | Same as call in the line below. |
| 18 | call_user_func_array() | JROOT/libraries/src/Cache/Controller/CallbackController.php:173 |
| 17 | Joomla\CMS\Cache\Controller\CallbackController->get() | JROOT/libraries/src/Helper/ModuleHelper.php:441 |
| 16 | Joomla\CMS\Helper\ModuleHelper::getModuleList() | JROOT/libraries/src/Helper/ModuleHelper.php:371 |
| 15 | Joomla\CMS\Helper\ModuleHelper::load() | JROOT/libraries/src/Helper/ModuleHelper.php:87 |
| 14 | Joomla\CMS\Helper\ModuleHelper::getModules() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1569 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php:38 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:212 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.02 ms After last query: 0.95 ms Query memory: 0.029 MB Memory before query: 31.960 MB Rows returned: 4
SELECT `group_id`
FROM `l6r3h_user_usergroup_map`
WHERE `user_id` = '43'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_user_usergroup_map | NULL | ref | PRIMARY | PRIMARY | 4 | const | 4 | 100.00 | Using index |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 28 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1550 |
| 27 | JDatabaseDriver->loadColumn() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 26 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/includes/acl/acl.php:58 |
| 25 | EasyBlogAcl::getRuleSet() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:298 |
| 24 | EB::acl() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:2930 |
| 23 | EB::isBlogger() | JROOT/administrator/components/com_easyblog/includes/profile/adapters/default/client.php:32 |
| 22 | EasyBlogProfileDefault->getLink() | JROOT/administrator/components/com_easyblog/includes/profile/profile.php:44 |
| 21 | EasyBlogProfile->getLink() | JROOT/administrator/components/com_easyblog/tables/profile.php:524 |
| 20 | EasyBlogTableProfile->getProfileLink() | JROOT/administrator/components/com_easyblog/includes/post/post.php:4746 |
| 19 | EasyBlogPost->getAuthorPermalink() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:29 |
| 18 | EasyBlogThemesHelperPostList->authorAvatar() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 17 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/bluedream/listing/default.php:21 |
| 16 | include JROOT/components/com_easyblog/themes/bluedream/listing/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 15 | EasyBlogThemes->output() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:291 |
| 14 | EasyBlogThemesHelperPostList->item() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 13 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php:48 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:212 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.55 ms After last query: 0.05 ms Query memory: 0.048 MB Memory before query: 31.973 MB Rows returned: 204
SELECT *
FROM `l6r3h_easyblog_acl_group`
WHERE `content_id` IN (2, 3, 9, 10)
AND `type`='
group'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_easyblog_acl_group | NULL | ALL | easyblog_post_acl_content_type | NO INDEX KEY COULD BE USED | NULL | NULL | 561 | 36.36 | Using where |
| Status | Duration |
|---|
| starting | 0.45 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.05 ms |
| preparing | 0.09 ms |
| executing | 0.01 ms |
| Sending data | 0.94 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.05 ms |
| # | Caller | File and line number |
|---|
| 29 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 28 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 27 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/includes/acl/acl.php:151 |
| 26 | EasyBlogAcl::getEasyBlogAclGroups() | JROOT/administrator/components/com_easyblog/includes/acl/acl.php:65 |
| 25 | EasyBlogAcl::getRuleSet() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:298 |
| 24 | EB::acl() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:2930 |
| 23 | EB::isBlogger() | JROOT/administrator/components/com_easyblog/includes/profile/adapters/default/client.php:32 |
| 22 | EasyBlogProfileDefault->getLink() | JROOT/administrator/components/com_easyblog/includes/profile/profile.php:44 |
| 21 | EasyBlogProfile->getLink() | JROOT/administrator/components/com_easyblog/tables/profile.php:524 |
| 20 | EasyBlogTableProfile->getProfileLink() | JROOT/administrator/components/com_easyblog/includes/post/post.php:4746 |
| 19 | EasyBlogPost->getAuthorPermalink() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:29 |
| 18 | EasyBlogThemesHelperPostList->authorAvatar() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 17 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/bluedream/listing/default.php:21 |
| 16 | include JROOT/components/com_easyblog/themes/bluedream/listing/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 15 | EasyBlogThemes->output() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:291 |
| 14 | EasyBlogThemesHelperPostList->item() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 13 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php:48 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:212 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.00 ms After last query: 1.06 ms Query memory: 0.029 MB Memory before query: 32.146 MB Rows returned: 1
SELECT `template`
FROM `l6r3h_template_styles`
WHERE `home`!='0'
AND `client_id`='0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_template_styles | NULL | ALL | idx_client_id,idx_client_id_home | NO INDEX KEY COULD BE USED | NULL | NULL | 5 | 48.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 28 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 27 | JDatabaseDriver->loadResult() | JROOT/libraries/foundry/helper.php:553 |
| 26 | FH::getCurrentTemplate() | JROOT/administrator/components/com_easyblog/includes/avatar/adapters/default/client.php:40 |
| 25 | EasyBlogAvatarDefault->getAvatar() | JROOT/administrator/components/com_easyblog/includes/avatar/avatar.php:41 |
| 24 | EasyBlogAvatar->getAvatarURL() | JROOT/administrator/components/com_easyblog/tables/profile.php:351 |
| 23 | EasyBlogTableProfile->getAvatar() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/avatar.php:43 |
| 22 | EasyBlogThemesHelperAvatar->user() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 21 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/wireframe/helpers/post/list/author.avatar.php:14 |
| 20 | include JROOT/components/com_easyblog/themes/wireframe/helpers/post/list/author.avatar.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 19 | EasyBlogThemes->output() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:35 |
| 18 | EasyBlogThemesHelperPostList->authorAvatar() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 17 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/bluedream/listing/default.php:21 |
| 16 | include JROOT/components/com_easyblog/themes/bluedream/listing/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 15 | EasyBlogThemes->output() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:291 |
| 14 | EasyBlogThemesHelperPostList->item() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 13 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php:48 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:212 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.14 ms After last query: 8.10 ms Query memory: 0.035 MB Memory before query: 32.905 MB Rows returned: 0
SELECT DISTINCT a.id, a.title, a.name, a.checked_out, a.checked_out_time, a.note, a.state, a.access, a.created_time, a.created_user_id, a.ordering, a.language, a.fieldparams, a.params, a.type, a.default_value, a.context, a.group_id, a.label, a.description, a.required,l.title AS language_title, l.image AS language_image,uc.name AS editor,ag.title AS access_level,ua.name AS author_name,g.title AS group_title, g.access as group_access, g.state AS group_state, g.note as group_note
FROM l6r3h_fields AS a
LEFT JOIN `l6r3h_languages` AS l
ON l.lang_code = a.language
LEFT JOIN l6r3h_users AS uc
ON uc.id=a.checked_out
LEFT JOIN l6r3h_viewlevels AS ag
ON ag.id = a.access
LEFT JOIN l6r3h_users AS ua
ON ua.id = a.created_user_id
LEFT JOIN l6r3h_fields_groups AS g
ON g.id = a.group_id
LEFT JOIN `l6r3h_fields_categories` AS fc
ON fc.field_id = a.id
WHERE a.context = 'easyblog.blog'
AND (fc.category_id IS NULL OR fc.category_id IN (9,0))
AND a.access IN (1,1,6)
AND (a.group_id = 0 OR g.access IN (1,1,6))
AND a.state = 1
AND (a.group_id = 0 OR g.state = 1)
ORDER BY a.ordering ASC
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | a | NULL | ref | idx_state,idx_access,idx_context | idx_state | 1 | const | 1 | 100.00 | Using index condition; Using where; Using temporary; Using filesort |
| 1 | SIMPLE | l | NULL | eq_ref | idx_langcode | idx_langcode | 28 | db597855425.a.language | 1 | 100.00 | Using where |
| 1 | SIMPLE | uc | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.a.checked_out | 1 | 100.00 | NULL |
| 1 | SIMPLE | ag | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.a.access | 1 | 100.00 | Using where |
| 1 | SIMPLE | ua | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.a.created_user_id | 1 | 100.00 | Using where |
| 1 | SIMPLE | g | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.a.group_id | 1 | 100.00 | Using where |
| 1 | SIMPLE | fc | NULL | ref | PRIMARY | PRIMARY | 4 | db597855425.a.id | 1 | 100.00 | Using where; Using index; Distinct |
| Status | Duration |
|---|
| starting | 0.11 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.00 ms |
| checking permissions | 0.00 ms |
| checking permissions | 0.00 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.00 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.31 ms |
| init | 0.06 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.11 ms |
| preparing | 0.03 ms |
| Creating tmp table | 0.08 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.22 ms |
| Creating sort index | 0.03 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| removing tmp table | 0.06 ms |
| query end | 0.01 ms |
| closing tables | 0.02 ms |
| freeing items | 1.59 ms |
| cleaning up | 0.04 ms |
| # | Caller | File and line number |
|---|
| 31 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 30 | JDatabaseDriver->loadObjectList() | JROOT/libraries/src/MVC/Model/BaseDatabaseModel.php:322 |
| 29 | Joomla\CMS\MVC\Model\BaseDatabaseModel->_getList() | JROOT/administrator/components/com_fields/models/fields.php:333 |
| 28 | FieldsModelFields->_getList() | JROOT/libraries/src/MVC/Model/ListModel.php:194 |
| 27 | Joomla\CMS\MVC\Model\ListModel->getItems() | JROOT/administrator/components/com_fields/helpers/fields.php:136 |
| 26 | FieldsHelper::getFields() | JROOT/plugins/system/fields/fields.php:495 |
| 25 | PlgSystemFields->onContentPrepare() | JROOT/libraries/joomla/event/event.php:70 |
| 24 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 23 | JEventDispatcher->trigger() | JROOT/administrator/components/com_easyblog/includes/dispatcher/dispatcher.php:45 |
| 22 | EasyBlogDispatcher->trigger() | JROOT/administrator/components/com_easyblog/includes/triggers/triggers.php:48 |
| 21 | EasyBlogTriggers->trigger() | JROOT/administrator/components/com_easyblog/includes/post/post.php:5872 |
| 20 | EasyBlogPost->prepareContent() | JROOT/administrator/components/com_easyblog/includes/post/post.php:5291 |
| 19 | EasyBlogPost->getIntro() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:68 |
| 18 | EasyBlogThemesHelperPostList->content() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 17 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/bluedream/listing/default.php:49 |
| 16 | include JROOT/components/com_easyblog/themes/bluedream/listing/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 15 | EasyBlogThemes->output() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:291 |
| 14 | EasyBlogThemesHelperPostList->item() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 13 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php:48 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:212 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.68 ms After last query: 6.74 ms Query memory: 0.041 MB Memory before query: 33.813 MB Rows returned: 41
SHOW FULL COLUMNS
FROM `l6r3h_sh404sef_metas`
EXPLAIN not possible on query: SHOW FULL COLUMNS FROM `l6r3h_sh404sef_metas`
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.27 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Opening tables | 0.08 ms |
| checking permissions | 0.03 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| removing tmp table | 0.09 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 35 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 34 | JDatabaseDriver->loadObjectList() | JROOT/libraries/joomla/database/driver/mysqli.php:448 |
| 33 | JDatabaseDriverMysqli->getTableColumns() | JROOT/libraries/src/Table/Table.php:261 |
| 32 | Joomla\CMS\Table\Table->getFields() | JROOT/libraries/src/Table/Table.php:180 |
| 31 | Joomla\CMS\Table\Table->__construct() | JROOT/administrator/components/com_sh404sef/tables/metas.php:138 |
| 30 | Sh404sefTableMetas->__construct() | JROOT/libraries/src/Table/Table.php:328 |
| 29 | Joomla\CMS\Table\Table::getInstance() | JROOT/administrator/components/com_sh404sef/models/metas.php:37 |
| 28 | Sh404sefModelMetas->getCustomMetaData() | JROOT/administrator/components/com_sh404sef/helpers/metadata.php:92 |
| 27 | Sh404sefHelperMetadata::getCustomMetaDataFromDb() | JROOT/plugins/system/sh404sef/sh404sef.php:515 |
| 26 | plgSystemSh404sef->searchOGPImage() | JROOT/plugins/system/sh404sef/sh404sef.php:347 |
| 25 | plgSystemSh404sef->onContentPrepare() | JROOT/libraries/joomla/event/event.php:70 |
| 24 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 23 | JEventDispatcher->trigger() | JROOT/administrator/components/com_easyblog/includes/dispatcher/dispatcher.php:45 |
| 22 | EasyBlogDispatcher->trigger() | JROOT/administrator/components/com_easyblog/includes/triggers/triggers.php:48 |
| 21 | EasyBlogTriggers->trigger() | JROOT/administrator/components/com_easyblog/includes/post/post.php:5872 |
| 20 | EasyBlogPost->prepareContent() | JROOT/administrator/components/com_easyblog/includes/post/post.php:5291 |
| 19 | EasyBlogPost->getIntro() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:68 |
| 18 | EasyBlogThemesHelperPostList->content() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 17 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/bluedream/listing/default.php:49 |
| 16 | include JROOT/components/com_easyblog/themes/bluedream/listing/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 15 | EasyBlogThemes->output() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:291 |
| 14 | EasyBlogThemesHelperPostList->item() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 13 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php:48 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:212 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.10 ms After last query: 0.14 ms Query memory: 0.032 MB Memory before query: 33.870 MB Rows returned: 0
SELECT *
FROM l6r3h_sh404sef_metas
WHERE `newurl`='index.php?option=com_easyblog&Itemid=486&id=9&lang=en&layout=listings&
limit=10&limitstart=40&view=categories';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_metas | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 33 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 32 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 31 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 30 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 29 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/models/metas.php:38 |
| 28 | Sh404sefModelMetas->getCustomMetaData() | JROOT/administrator/components/com_sh404sef/helpers/metadata.php:92 |
| 27 | Sh404sefHelperMetadata::getCustomMetaDataFromDb() | JROOT/plugins/system/sh404sef/sh404sef.php:515 |
| 26 | plgSystemSh404sef->searchOGPImage() | JROOT/plugins/system/sh404sef/sh404sef.php:347 |
| 25 | plgSystemSh404sef->onContentPrepare() | JROOT/libraries/joomla/event/event.php:70 |
| 24 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 23 | JEventDispatcher->trigger() | JROOT/administrator/components/com_easyblog/includes/dispatcher/dispatcher.php:45 |
| 22 | EasyBlogDispatcher->trigger() | JROOT/administrator/components/com_easyblog/includes/triggers/triggers.php:48 |
| 21 | EasyBlogTriggers->trigger() | JROOT/administrator/components/com_easyblog/includes/post/post.php:5872 |
| 20 | EasyBlogPost->prepareContent() | JROOT/administrator/components/com_easyblog/includes/post/post.php:5291 |
| 19 | EasyBlogPost->getIntro() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:68 |
| 18 | EasyBlogThemesHelperPostList->content() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 17 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/bluedream/listing/default.php:49 |
| 16 | include JROOT/components/com_easyblog/themes/bluedream/listing/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 15 | EasyBlogThemes->output() | JROOT/administrator/components/com_easyblog/includes/themes/helpers/post/list.php:291 |
| 14 | EasyBlogThemesHelperPostList->item() | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:430 |
| 13 | EasyBlogThemes->html() | JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php:48 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/categories/item/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:212 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.36 ms After last query: 34.95 ms Query memory: 0.028 MB Memory before query: 34.710 MB Rows returned: 1
SELECT `template`
FROM `l6r3h_template_styles`
WHERE `home` = '1'
AND `client_id` ='0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_template_styles | NULL | ref | idx_client_id,idx_client_id_home | idx_client_id_home | 29 | const,const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.08 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.02 ms |
| System lock | 0.02 ms |
| optimizing | 0.02 ms |
| statistics | 0.09 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 25 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 24 | JDatabaseDriver->loadResult() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:160 |
| 23 | ToolbarThemes->getCurrentTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:175 |
| 22 | ToolbarThemes->getCurrentTemplatePath() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:113 |
| 21 | ToolbarThemes->setTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:94 |
| 20 | ToolbarThemes->output() | JROOT/modules/mod_stackideas_toolbar/includes/menu/menu.php:44 |
| 19 | ToolbarMenu->render() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:27 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.27 ms After last query: 0.33 ms Query memory: 0.027 MB Memory before query: 34.738 MB Rows returned: 0
SELECT `id`
FROM `l6r3h_menu`
WHERE (`link`='index.php?option=com_easyblog&view=search' OR `link` LIKE 'index.php?option=com_easyblog&view=search&
limit=%')
AND `published`='1'
AND `client_id`='0'
AND (`language`='en-GB' OR `language`='' OR `language`='*')
ORDER BY `id` ASC
LIMIT 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_menu | NULL | index | idx_client_id_parent_id_alias_language,idx_language | PRIMARY | 4 | NULL | 2 | 2.50 | Using where |
| Status | Duration |
|---|
| starting | 0.13 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.03 ms |
| init | 0.05 ms |
| System lock | 0.02 ms |
| optimizing | 0.03 ms |
| statistics | 0.14 ms |
| preparing | 0.04 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.64 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.02 ms |
| freeing items | 0.06 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 24 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 23 | JDatabaseDriver->loadResult() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 22 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/includes/router.php:1563 |
| 21 | EBR::getItemId() | JROOT/modules/mod_stackideas_toolbar/includes/adapter/easyblog/easyblog.php:41 |
| 20 | ToolbarAdapterEasyblog->getSearchRoute() | JROOT/modules/mod_stackideas_toolbar/includes/search/search.php:48 |
| 19 | ToolbarSearch->render() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:29 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.12 ms After last query: 0.06 ms Query memory: 0.027 MB Memory before query: 34.749 MB Rows returned: 0
SELECT `id`
FROM `l6r3h_menu`
WHERE `link` LIKE 'index.php?option=com_easyblog&view=search%'
AND `published`='1'
AND `client_id`='0'
AND (`language`='en-GB' OR `language`='' OR `language`='*')
LIMIT 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_menu | NULL | ref | idx_client_id_parent_id_alias_language,idx_language | idx_client_id_parent_id_alias_language | 1 | const | 100 | 1.11 | Using index condition; Using where |
| Status | Duration |
|---|
| starting | 0.07 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.11 ms |
| preparing | 0.03 ms |
| executing | 0.01 ms |
| Sending data | 0.81 ms |
| end | 0.02 ms |
| query end | 0.02 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 24 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 23 | JDatabaseDriver->loadResult() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 22 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/includes/router.php:1576 |
| 21 | EBR::getItemId() | JROOT/modules/mod_stackideas_toolbar/includes/adapter/easyblog/easyblog.php:41 |
| 20 | ToolbarAdapterEasyblog->getSearchRoute() | JROOT/modules/mod_stackideas_toolbar/includes/search/search.php:48 |
| 19 | ToolbarSearch->render() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:29 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.48 ms After last query: 0.06 ms Query memory: 0.028 MB Memory before query: 34.761 MB Rows returned: 1
SELECT `id`
FROM `l6r3h_menu`
WHERE `link`='index.php?option=com_easyblog&view=latest'
AND `published`='1'
AND `client_id`='0'
AND (`language`='en-GB' OR `language`='' OR `language`='*')
LIMIT 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_menu | NULL | ref | idx_client_id_parent_id_alias_language,idx_language | idx_client_id_parent_id_alias_language | 1 | const | 100 | 1.00 | Using index condition; Using where |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.11 ms |
| preparing | 0.03 ms |
| executing | 0.01 ms |
| Sending data | 0.17 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 24 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 23 | JDatabaseDriver->loadResult() | JROOT/administrator/components/com_easyblog/includes/utils.php:296 |
| 22 | EasyBlogDbJoomla->__call() | JROOT/administrator/components/com_easyblog/includes/router.php:1589 |
| 21 | EBR::getItemId() | JROOT/modules/mod_stackideas_toolbar/includes/adapter/easyblog/easyblog.php:41 |
| 20 | ToolbarAdapterEasyblog->getSearchRoute() | JROOT/modules/mod_stackideas_toolbar/includes/search/search.php:48 |
| 19 | ToolbarSearch->render() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:29 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.29 ms After last query: 0.05 ms Query memory: 0.028 MB Memory before query: 34.774 MB Rows returned: 1
SELECT `template`
FROM `l6r3h_template_styles`
WHERE `home` = '1'
AND `client_id` ='0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_template_styles | NULL | ref | idx_client_id,idx_client_id_home | idx_client_id_home | 29 | const,const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.10 ms |
| preparing | 0.03 ms |
| executing | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.02 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 25 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 24 | JDatabaseDriver->loadResult() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:160 |
| 23 | ToolbarThemes->getCurrentTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:175 |
| 22 | ToolbarThemes->getCurrentTemplatePath() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:113 |
| 21 | ToolbarThemes->setTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:94 |
| 20 | ToolbarThemes->output() | JROOT/modules/mod_stackideas_toolbar/includes/search/search.php:48 |
| 19 | ToolbarSearch->render() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:29 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.27 ms After last query: 0.15 ms Query memory: 0.030 MB Memory before query: 34.810 MB Rows returned: 1
SELECT `template`
FROM `l6r3h_template_styles`
WHERE `home` = '1'
AND `client_id` ='0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_template_styles | NULL | ref | idx_client_id,idx_client_id_home | idx_client_id_home | 29 | const,const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.02 ms |
| optimizing | 0.02 ms |
| statistics | 0.07 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 29 | JDatabaseDriver->loadResult() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:160 |
| 28 | ToolbarThemes->getCurrentTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:175 |
| 27 | ToolbarThemes->getCurrentTemplatePath() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:113 |
| 26 | ToolbarThemes->setTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:94 |
| 25 | ToolbarThemes->output() | JROOT/modules/mod_stackideas_toolbar/includes/search/search.php:81 |
| 24 | ToolbarSearch->categories() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 23 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/search/default.php:18 |
| 22 | include JROOT/modules/mod_stackideas_toolbar/tmpl/search/default.php | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:137 |
| 21 | ToolbarThemes->parse() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:96 |
| 20 | ToolbarThemes->output() | JROOT/modules/mod_stackideas_toolbar/includes/search/search.php:48 |
| 19 | ToolbarSearch->render() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:29 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.57 ms After last query: 3.86 ms Query memory: 0.030 MB Memory before query: 34.960 MB Rows returned: 1
SELECT `template`
FROM `l6r3h_template_styles`
WHERE `home` = '1'
AND `client_id` ='0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_template_styles | NULL | ref | idx_client_id,idx_client_id_home | idx_client_id_home | 29 | const,const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.07 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.08 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.04 ms |
| freeing items | 0.06 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 29 | JDatabaseDriver->loadResult() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:160 |
| 28 | ToolbarThemes->getCurrentTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:175 |
| 27 | ToolbarThemes->getCurrentTemplatePath() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:113 |
| 26 | ToolbarThemes->setTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:94 |
| 25 | ToolbarThemes->output() | JROOT/modules/mod_stackideas_toolbar/includes/search/search.php:128 |
| 24 | ToolbarSearch->input() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 23 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/search/default.php:22 |
| 22 | include JROOT/modules/mod_stackideas_toolbar/tmpl/search/default.php | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:137 |
| 21 | ToolbarThemes->parse() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:96 |
| 20 | ToolbarThemes->output() | JROOT/modules/mod_stackideas_toolbar/includes/search/search.php:48 |
| 19 | ToolbarSearch->render() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:29 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.51 ms After last query: 0.74 ms Query memory: 0.028 MB Memory before query: 34.980 MB Rows returned: 1
SELECT `template`
FROM `l6r3h_template_styles`
WHERE `home` = '1'
AND `client_id` ='0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_template_styles | NULL | ref | idx_client_id,idx_client_id_home | idx_client_id_home | 29 | const,const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.07 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.06 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.07 ms |
| # | Caller | File and line number |
|---|
| 25 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 24 | JDatabaseDriver->loadResult() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:160 |
| 23 | ToolbarThemes->getCurrentTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:175 |
| 22 | ToolbarThemes->getCurrentTemplatePath() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:113 |
| 21 | ToolbarThemes->setTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:94 |
| 20 | ToolbarThemes->output() | JROOT/modules/mod_stackideas_toolbar/includes/action/action.php:165 |
| 19 | ToolbarAction->search() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:35 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.41 ms After last query: 0.59 ms Query memory: 0.028 MB Memory before query: 35.030 MB Rows returned: 1
SELECT `template`
FROM `l6r3h_template_styles`
WHERE `home` = '1'
AND `client_id` ='0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_template_styles | NULL | ref | idx_client_id,idx_client_id_home | idx_client_id_home | 29 | const,const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.04 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.03 ms |
| statistics | 0.21 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.04 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 25 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 24 | JDatabaseDriver->loadResult() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:160 |
| 23 | ToolbarThemes->getCurrentTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:175 |
| 22 | ToolbarThemes->getCurrentTemplatePath() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:113 |
| 21 | ToolbarThemes->setTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:94 |
| 20 | ToolbarThemes->output() | JROOT/modules/mod_stackideas_toolbar/includes/action/action.php:193 |
| 19 | ToolbarAction->subscriptions() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:39 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.42 ms After last query: 3.76 ms Query memory: 0.028 MB Memory before query: 35.331 MB Rows returned: 1
SELECT `template`
FROM `l6r3h_template_styles`
WHERE `home` = '1'
AND `client_id` ='0'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_template_styles | NULL | ref | idx_client_id,idx_client_id_home | idx_client_id_home | 29 | const,const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.07 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.02 ms |
| optimizing | 0.02 ms |
| statistics | 0.08 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 26 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 25 | JDatabaseDriver->loadResult() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:160 |
| 24 | ToolbarThemes->getCurrentTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:175 |
| 23 | ToolbarThemes->getCurrentTemplatePath() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:113 |
| 22 | ToolbarThemes->setTemplate() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:94 |
| 21 | ToolbarThemes->output() | JROOT/modules/mod_stackideas_toolbar/includes/dropdown/dropdown.php:93 |
| 20 | ToolbarDropdown->guest() | JROOT/modules/mod_stackideas_toolbar/includes/dropdown/dropdown.php:34 |
| 19 | ToolbarDropdown->user() | JROOT/modules/mod_stackideas_toolbar/includes/themes/themes.php:83 |
| 18 | ToolbarThemes->html() | JROOT/modules/mod_stackideas_toolbar/tmpl/default.php:41 |
| 17 | require JROOT/modules/mod_stackideas_toolbar/tmpl/default.php | JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php:43 |
| 16 | include JROOT/modules/mod_stackideas_toolbar/mod_stackideas_toolbar.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 15 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 14 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:1580 |
| 13 | EB::renderModule() | JROOT/components/com_easyblog/themes/wireframe/structure/default.php:65 |
| 12 | include JROOT/components/com_easyblog/themes/wireframe/structure/default.php | JROOT/administrator/components/com_easyblog/includes/themes/themes.php:468 |
| 11 | EasyBlogThemes->output() | JROOT/components/com_easyblog/views/views.php:286 |
| 10 | EasyBlogView->display() | JROOT/components/com_easyblog/views/categories/view.html.php:431 |
| 9 | EasyBlogViewCategories->listings() | JROOT/components/com_easyblog/controllers/controller.php:101 |
| 8 | EasyBlogController->display() | JROOT/libraries/src/MVC/Controller/BaseController.php:702 |
| 7 | Joomla\CMS\MVC\Controller\BaseController->execute() | JROOT/components/com_easyblog/easyblog.php:45 |
| 6 | require_once JROOT/components/com_easyblog/easyblog.php | JROOT/libraries/src/Component/ComponentHelper.php:402 |
| 5 | Joomla\CMS\Component\ComponentHelper::executeComponent() | JROOT/libraries/src/Component/ComponentHelper.php:377 |
| 4 | Joomla\CMS\Component\ComponentHelper::renderComponent() | JROOT/libraries/src/Application/SiteApplication.php:194 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.63 ms After last query: 7.04 ms Query memory: 0.021 MB Memory before query: 35.576 MB Rows returned: 0
SELECT `pageid`
FROM l6r3h_sh404sef_pageids
WHERE `newurl`='index.php?option=com_easyblog&Itemid=486&id=9&lang=en&layout=listings&
limit=10&limitstart=40&view=categories';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_pageids | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.02 ms |
| optimizing | 0.02 ms |
| statistics | 0.07 ms |
| preparing | 0.02 ms |
| executing | 0.02 ms |
| Sending data | 0.06 ms |
| end | 0.01 ms |
| query end | 0.02 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 12 | JDatabaseDriver->loadResult() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:687 |
| 11 | ShlDbClass->loadResult() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:377 |
| 10 | ShlDbClass->shlLoadResult() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:483 |
| 9 | ShlDbHelper::selectResult() | JROOT/administrator/components/com_sh404sef/helpers/shurl.php:57 |
| 8 | Sh404sefHelperShurl::updateShurls() | JROOT/plugins/system/sh404sef/sh404sef.php:283 |
| 7 | plgSystemSh404sef->onAfterDispatch() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/SiteApplication.php:199 |
| 3 | Joomla\CMS\Application\SiteApplication->dispatch() | JROOT/libraries/src/Application/SiteApplication.php:233 |
| 2 | Joomla\CMS\Application\SiteApplication->doExecute() | JROOT/libraries/src/Application/CMSApplication.php:225 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.37 ms After last query: 6.35 ms Query memory: 0.029 MB Memory before query: 35.755 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&Itemid=427&lang=en&view=itissueslist';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.03 ms |
| init | 0.03 ms |
| System lock | 0.02 ms |
| optimizing | 0.03 ms |
| statistics | 0.10 ms |
| preparing | 0.03 ms |
| executing | 0.01 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.02 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_menu/helper.php:139 |
| 11 | ModMenuHelper::getList() | JROOT/modules/mod_menu/mod_menu.php:15 |
| 10 | include JROOT/modules/mod_menu/mod_menu.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.62 ms After last query: 4.84 ms Query memory: 0.029 MB Memory before query: 36.350 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&Itemid=1824&lang=en&view=itissueslist';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.02 ms |
| optimizing | 0.02 ms |
| statistics | 0.09 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.34 ms |
| end | 0.02 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_menu/helper.php:139 |
| 11 | ModMenuHelper::getList() | JROOT/modules/mod_menu/mod_menu.php:15 |
| 10 | include JROOT/modules/mod_menu/mod_menu.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.38 ms After last query: 0.46 ms Query memory: 0.029 MB Memory before query: 36.376 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&Itemid=428&lang=en&view=itissueslist';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.02 ms |
| optimizing | 0.02 ms |
| statistics | 0.12 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.05 ms |
| end | 0.02 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_menu/helper.php:139 |
| 11 | ModMenuHelper::getList() | JROOT/modules/mod_menu/mod_menu.php:15 |
| 10 | include JROOT/modules/mod_menu/mod_menu.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.63 ms After last query: 0.50 ms Query memory: 0.029 MB Memory before query: 36.403 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&Itemid=3577&lang=en&view=itissueslist';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.09 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.03 ms |
| init | 0.04 ms |
| System lock | 0.02 ms |
| optimizing | 0.04 ms |
| statistics | 0.10 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.02 ms |
| closing tables | 0.02 ms |
| freeing items | 0.88 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_menu/helper.php:139 |
| 11 | ModMenuHelper::getList() | JROOT/modules/mod_menu/mod_menu.php:15 |
| 10 | include JROOT/modules/mod_menu/mod_menu.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.83 ms After last query: 0.44 ms Query memory: 0.029 MB Memory before query: 36.430 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&Itemid=4059&lang=en&view=itissueslist';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.53 ms |
| Opening tables | 0.02 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.05 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.14 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_menu/helper.php:139 |
| 11 | ModMenuHelper::getList() | JROOT/modules/mod_menu/mod_menu.php:15 |
| 10 | include JROOT/modules/mod_menu/mod_menu.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.17 ms After last query: 2.34 ms Query memory: 0.026 MB Memory before query: 36.571 MB Rows returned: 1
SELECT *
FROM `l6r3h_kunena_configuration`
WHERE `id`=1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_kunena_configuration | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.12 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.03 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 23 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1465 |
| 22 | JDatabaseDriver->loadAssoc() | JROOT/libraries/kunena/config.php:1437 |
| 21 | KunenaConfig->load() | JROOT/libraries/kunena/config.php:1410 |
| 20 | KunenaConfig::getInstance() | JROOT/components/com_kunena/router.php:42 |
| 19 | KunenaBuildRoute() | JROOT/libraries/src/Component/Router/RouterLegacy.php:69 |
| 18 | Joomla\CMS\Component\Router\RouterLegacy->build() | JROOT/libraries/src/Router/SiteRouter.php:532 |
| 17 | Joomla\CMS\Router\SiteRouter->buildSefRoute() | JROOT/libraries/src/Router/SiteRouter.php:502 |
| 16 | Joomla\CMS\Router\SiteRouter->_buildSefRoute() | JROOT/libraries/src/Router/Router.php:281 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_menu/helper.php:139 |
| 11 | ModMenuHelper::getList() | JROOT/modules/mod_menu/mod_menu.php:15 |
| 10 | include JROOT/modules/mod_menu/mod_menu.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.02 ms After last query: 6.63 ms Query memory: 0.029 MB Memory before query: 36.915 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&Itemid=416&lang=en&layout=edit&view=form';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.05 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 31 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 30 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 29 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 28 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 27 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 26 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 25 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 24 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 23 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 22 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 21 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 20 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 19 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 18 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 17 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 16 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 15 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 14 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 13 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_osdonate/library/Free/Helper.php:202 |
| 12 | Alledia\OSDonate\Free\Helper->getReturnMenus() | JROOT/modules/mod_osdonate/library/Free/Helper.php:87 |
| 11 | Alledia\OSDonate\Free\Helper->__construct() | JROOT/modules/mod_osdonate/mod_osdonate.php:51 |
| 10 | include JROOT/modules/mod_osdonate/mod_osdonate.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.57 ms After last query: 4.48 ms Query memory: 0.041 MB Memory before query: 37.509 MB Rows returned: 337
SHOW TABLES
EXPLAIN not possible on query: SHOW TABLES
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| checking permissions | 0.75 ms |
| Sending data | 0.58 ms |
| end | 0.02 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| removing tmp table | 0.02 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 18 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1550 |
| 17 | JDatabaseDriver->loadColumn() | JROOT/libraries/joomla/database/driver/mysqli.php:505 |
| 16 | JDatabaseDriverMysqli->getTableList() | JROOT/administrator/components/com_acymailing/compat/joomla.php:724 |
| 15 | acymailing_getTableList() | JROOT/administrator/components/com_acymailing/classes/cpanel.php:18 |
| 14 | cpanelClass->load() | JROOT/administrator/components/com_acymailing/helpers/helper.php:523 |
| 13 | acymailing_config() | JROOT/administrator/components/com_acymailing/compat/joomla.php:1075 |
| 12 | include_once JROOT/administrator/components/com_acymailing/compat/joomla.php | JROOT/administrator/components/com_acymailing/helpers/helper.php:25 |
| 11 | include_once JROOT/administrator/components/com_acymailing/helpers/helper.php | JROOT/modules/mod_acymailing/mod_acymailing.php:13 |
| 10 | include JROOT/modules/mod_acymailing/mod_acymailing.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.52 ms After last query: 0.11 ms Query memory: 0.035 MB Memory before query: 37.554 MB Rows returned: 159
SELECT *
FROM l6r3h_acymailing_config
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_acymailing_config | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 159 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.07 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.00 ms |
| statistics | 0.01 ms |
| preparing | 0.02 ms |
| executing | 0.00 ms |
| Sending data | 0.41 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 17 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 16 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_acymailing/compat/joomla.php:628 |
| 15 | acymailing_loadObjectList() | JROOT/administrator/components/com_acymailing/classes/cpanel.php:23 |
| 14 | cpanelClass->load() | JROOT/administrator/components/com_acymailing/helpers/helper.php:523 |
| 13 | acymailing_config() | JROOT/administrator/components/com_acymailing/compat/joomla.php:1075 |
| 12 | include_once JROOT/administrator/components/com_acymailing/compat/joomla.php | JROOT/administrator/components/com_acymailing/helpers/helper.php:25 |
| 11 | include_once JROOT/administrator/components/com_acymailing/helpers/helper.php | JROOT/modules/mod_acymailing/mod_acymailing.php:13 |
| 10 | include JROOT/modules/mod_acymailing/mod_acymailing.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.12 ms After last query: 3.34 ms Query memory: 0.023 MB Memory before query: 37.976 MB Rows returned: 3
SELECT *
FROM l6r3h_acymailing_list
WHERE type = 'list'
ORDER BY ordering ASC
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_acymailing_list | NULL | ALL | typeorderingindex,typeuseridindex | NO INDEX KEY COULD BE USED | NULL | NULL | 3 | 100.00 | Using where; Using filesort |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.08 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.03 ms |
| preparing | 0.01 ms |
| Sorting result | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| Creating sort index | 0.06 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 14 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 13 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_acymailing/compat/joomla.php:628 |
| 12 | acymailing_loadObjectList() | JROOT/administrator/components/com_acymailing/classes/list.php:30 |
| 11 | listClass->getLists() | JROOT/modules/mod_acymailing/mod_acymailing.php:149 |
| 10 | include JROOT/modules/mod_acymailing/mod_acymailing.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.03 ms After last query: 0.73 ms Query memory: 0.030 MB Memory before query: 38.047 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_acymailing&ctrl=archive&lang=en&listid=2-updates-
and-security-fixes';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.02 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.10 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.01 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 32 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 31 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 30 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 29 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 28 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 27 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 26 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 25 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 24 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 23 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 22 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 21 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 20 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 19 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 18 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 17 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 16 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 15 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 14 | Joomla\CMS\Router\Route::_() | JROOT/administrator/components/com_acymailing/compat/joomla.php:173 |
| 13 | acymailing_route() | JROOT/administrator/components/com_acymailing/compat/joomla.php:731 |
| 12 | acymailing_completeLink() | JROOT/modules/mod_acymailing/tmpl/tableless.php:53 |
| 11 | require JROOT/modules/mod_acymailing/tmpl/tableless.php | JROOT/modules/mod_acymailing/mod_acymailing.php:304 |
| 10 | include JROOT/modules/mod_acymailing/mod_acymailing.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 0.99 ms After last query: 0.37 ms Query memory: 0.030 MB Memory before query: 38.063 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_acymailing&ctrl=archive&lang=en&listid=1-mailing-list';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.02 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.02 ms |
| end | 0.00 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 32 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 31 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 30 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 29 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 28 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 27 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 26 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 25 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 24 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 23 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 22 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 21 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 20 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 19 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 18 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 17 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 16 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 15 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 14 | Joomla\CMS\Router\Route::_() | JROOT/administrator/components/com_acymailing/compat/joomla.php:173 |
| 13 | acymailing_route() | JROOT/administrator/components/com_acymailing/compat/joomla.php:731 |
| 12 | acymailing_completeLink() | JROOT/modules/mod_acymailing/tmpl/tableless.php:53 |
| 11 | require JROOT/modules/mod_acymailing/tmpl/tableless.php | JROOT/modules/mod_acymailing/mod_acymailing.php:304 |
| 10 | include JROOT/modules/mod_acymailing/mod_acymailing.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.08 ms After last query: 2.53 ms Query memory: 0.024 MB Memory before query: 38.197 MB Rows returned: 66
SELECT identifier
from `l6r3h_ipmap_robots`
WHERE state = 1
ORDER by ordering
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_ipmap_robots | NULL | ALL | idx_state | NO INDEX KEY COULD BE USED | NULL | NULL | 66 | 100.00 | Using where; Using filesort |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.06 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.02 ms |
| preparing | 0.01 ms |
| Sorting result | 0.00 ms |
| executing | 0.00 ms |
| Sending data | 0.01 ms |
| Creating sort index | 0.09 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1550 |
| 11 | JDatabaseDriver->loadColumn() | JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php:87 |
| 10 | include JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.08 ms After last query: 0.07 ms Query memory: 0.022 MB Memory before query: 38.216 MB Rows returned: 0
SELECT *
FROM `l6r3h_ipmap_location`
WHERE ipaddress = '3.138.138.144'
AND reason_id = 1
AND state = 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_ipmap_location | NULL | ALL | idx_state,idx_reasons | NO INDEX KEY COULD BE USED | NULL | NULL | 18 | 10.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.06 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.03 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 12 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_ipmapping/helpers/ipmapping.php:543 |
| 11 | IpmappingHelper::addToDb() | JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php:292 |
| 10 | include JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.08 ms After last query: 0.02 ms Query memory: 0.022 MB Memory before query: 38.222 MB Rows returned: 1
SELECT @n := IFNULL(MAX(ordering),1)
from `l6r3h_ipmap_location`
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_ipmap_location | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 18 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.04 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/administrator/components/com_ipmapping/helpers/ipmapping.php:551 |
| 11 | IpmappingHelper::addToDb() | JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php:292 |
| 10 | include JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 3.50 ms After last query: 0.05 ms Query memory: 0.006 MB Memory before query: 38.229 MB
INSERT INTO l6r3h_ipmap_location (`lat`, `lng`, `html5`, `ipaddress`,`time` ,`countryname`, `countrycode`, `cityname`, `referer`, `phrase`, `path`, `agent`,`reason_id`, `reason`, `src`,`logdate`, `created_by`, `created_on`, `ordering` )
VALUES ('0.00000000000','0.00000000000', '0', '3.138.138.144',1713255386,'UNKNOWN', 'ZZ', 'UNKNOWN', '', '', '/Blog/Categories/Miscellaneous/Page-5', 'claudebot', '1', 'visitors', '1', NOW(), 'agent', NOW(), @n+1 )
EXPLAIN not possible on query: INSERT INTO l6r3h_ipmap_location (`lat`, `lng`, `html5`, `ipaddress`,`time` ,`countryname`, `countrycode`, `cityname`, `referer`, `phrase`, `path`, `agent`,`reason_id`, `reason`, `src`,`logdate`, `created_by`, `created_on`, `ordering` ) VALUES ('0.00000000000','0.00000000000', '0', '3.138.138.144',1713255386,'UNKNOWN', 'ZZ', 'UNKNOWN', '', '', '/Blog/Categories/Miscellaneous/Page-5', 'claudebot', '1', 'visitors', '1', NOW(), 'agent', NOW(), @n+1 )
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| update | 0.12 ms |
| end | 0.01 ms |
| query end | 2.44 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/administrator/components/com_ipmapping/helpers/ipmapping.php:566 |
| 11 | IpmappingHelper::addToDb() | JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php:292 |
| 10 | include JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.06 ms After last query: 0.04 ms Query memory: 0.005 MB Memory before query: 38.231 MB
DELETE
FROM l6r3h_ipmap_location
WHERE ( time < '1713253986' )
AND reason_id = 1
AND state = 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | DELETE | l6r3h_ipmap_location | NULL | ALL | idx_state,idx_reasons | NO INDEX KEY COULD BE USED | NULL | NULL | 18 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.04 ms |
| updating | 0.05 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 11 | JDatabaseDriverMysqli->execute() | JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php:301 |
| 10 | include JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.17 ms After last query: 0.02 ms Query memory: 0.030 MB Memory before query: 38.237 MB Rows returned: 18
SELECT *
FROM l6r3h_ipmap_location
WHERE reason_id = 1
AND state = 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_ipmap_location | NULL | ALL | idx_state,idx_reasons | NO INDEX KEY COULD BE USED | NULL | NULL | 18 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.03 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.11 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 11 | JDatabaseDriver->loadObjectList() | JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php:305 |
| 10 | include JROOT/modules/mod_ipmapping_visitoragent/mod_ipmapping_visitoragent.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.06 ms After last query: 1.63 ms Query memory: 0.022 MB Memory before query: 38.264 MB Rows returned: 1
SELECT version
from `l6r3h_it_meta`
WHERE type = 'component'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_it_meta | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.08 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.03 ms |
| end | 0.02 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 11 | JDatabaseDriver->loadResult() | JROOT/modules/mod_latest_issues/mod_latest_issues.php:65 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.27 ms After last query: 0.04 ms Query memory: 0.022 MB Memory before query: 38.271 MB Rows returned: 5
SELECT i.id, i.actual_resolution_date, i.alias, i.issue_summary, p.title ,p.id AS project_id ,s.status_name AS status
FROM l6r3h_it_issues as i
LEFT JOIN l6r3h_it_projects as p
on i.related_project_id = p.id
LEFT JOIN l6r3h_it_status as s
on i.status = s.id
WHERE i.state = 1
AND i.public = 1
AND i.access IN (1,1,6)
AND p.access IN (1,1,6)
AND i.related_project_id IN ('117','120','114','33','119','37','112','103','115','108','106','116','121','122','113','118')
AND i.status IN ('1')
ORDER BY i.actual_resolution_date DESC
LIMIT 5
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | i | NULL | index_merge | l6r3h_it_issues_project_fk,l6r3h_it_issues_status_fk,idx_state | idx_state,l6r3h_it_issues_status_fk | 2,4 | NULL | 19 | 0.40 | Using intersect(idx_state,l6r3h_it_issues_status_fk); Using where; Using filesort |
| 1 | SIMPLE | p | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.i.related_project_id | 1 | 30.00 | Using where |
| 1 | SIMPLE | s | NULL | eq_ref | PRIMARY | PRIMARY | 4 | db597855425.i.status | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.07 ms |
| checking permissions | 0.01 ms |
| checking permissions | 0.00 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.61 ms |
| init | 0.05 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.14 ms |
| preparing | 0.02 ms |
| Sorting result | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.01 ms |
| Creating sort index | 0.32 ms |
| end | 0.01 ms |
| query end | 0.02 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 12 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 11 | JDatabaseDriver->loadObjectList() | JROOT/modules/mod_latest_issues/mod_latest_issues.php:113 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.28 ms After last query: 0.12 ms Query memory: 0.032 MB Memory before query: 38.281 MB Rows returned: 114
SELECT a.title AS text, a.id AS value, a.parent_id as parentid
FROM l6r3h_it_projects AS a
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | a | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 114 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.00 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.10 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 12 | JDatabaseDriver->loadObjectList() | JROOT/administrator/components/com_issuetracker/helpers/issuetracker.php:288 |
| 11 | IssueTrackerHelper::updateprojectname() | JROOT/modules/mod_latest_issues/mod_latest_issues.php:114 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 0.97 ms After last query: 0.08 ms Query memory: 0.022 MB Memory before query: 38.351 MB Rows returned: 1
SELECT id
FROM `l6r3h_it_projects`
WHERE title= 'Root'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_it_projects | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 114 | 10.00 | Using where |
| Status | Duration |
|---|
| starting | 0.02 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.06 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 14 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 13 | JDatabaseDriver->loadResult() | JROOT/administrator/components/com_issuetracker/helpers/issuetracker.php:248 |
| 12 | IssueTrackerHelper::ProjectTreeOption() | JROOT/administrator/components/com_issuetracker/helpers/issuetracker.php:293 |
| 11 | IssueTrackerHelper::updateprojectname() | JROOT/modules/mod_latest_issues/mod_latest_issues.php:114 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.00 ms After last query: 2.94 ms Query memory: 0.029 MB Memory before query: 38.315 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&id=524&lang=en&view=itissues';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.05 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_latest_issues/tmpl/default.php:52 |
| 11 | require JROOT/modules/mod_latest_issues/tmpl/default.php | JROOT/modules/mod_latest_issues/mod_latest_issues.php:116 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.32 ms After last query: 0.39 ms Query memory: 0.029 MB Memory before query: 38.343 MB Rows returned: 0
SELECT `id`
FROM `l6r3h_menu`
WHERE `link`='index.php?option=com_issuetracker&view=itissues'
AND `published`='1'
LIMIT 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_menu | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 251 | 1.00 | Using where |
| Status | Duration |
|---|
| starting | 0.02 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.25 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 28 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 27 | JDatabaseDriver->loadResult() | JROOT/components/com_issuetracker/helpers/route.php:240 |
| 26 | IssueTrackerHelperRoute::getItemId() | JROOT/components/com_issuetracker/sef_ext/com_issuetracker.php:101 |
| 25 | include JROOT/components/com_issuetracker/sef_ext/com_issuetracker.php | JROOT/components/com_sh404sef/sef_ext.php:388 |
| 24 | sef_404->create() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1798 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_latest_issues/tmpl/default.php:52 |
| 11 | require JROOT/modules/mod_latest_issues/tmpl/default.php | JROOT/modules/mod_latest_issues/mod_latest_issues.php:116 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.35 ms After last query: 0.05 ms Query memory: 0.029 MB Memory before query: 38.356 MB Rows returned: 1
SELECT `id`
FROM `l6r3h_menu`
WHERE `link` LIKE 'index.php?option=com_issuetracker&view=itissues%'
AND `published`='1'
LIMIT 1
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_menu | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 251 | 1.11 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.32 ms |
| end | 0.02 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 28 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 27 | JDatabaseDriver->loadResult() | JROOT/components/com_issuetracker/helpers/route.php:249 |
| 26 | IssueTrackerHelperRoute::getItemId() | JROOT/components/com_issuetracker/sef_ext/com_issuetracker.php:101 |
| 25 | include JROOT/components/com_issuetracker/sef_ext/com_issuetracker.php | JROOT/components/com_sh404sef/sef_ext.php:388 |
| 24 | sef_404->create() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1798 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_latest_issues/tmpl/default.php:52 |
| 11 | require JROOT/modules/mod_latest_issues/tmpl/default.php | JROOT/modules/mod_latest_issues/mod_latest_issues.php:116 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 0.97 ms After last query: 0.36 ms Query memory: 0.029 MB Memory before query: 38.356 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&id=522&lang=en&view=itissues';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.02 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.01 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_latest_issues/tmpl/default.php:52 |
| 11 | require JROOT/modules/mod_latest_issues/tmpl/default.php | JROOT/modules/mod_latest_issues/mod_latest_issues.php:116 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.74 ms After last query: 0.63 ms Query memory: 0.029 MB Memory before query: 38.370 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&id=521&lang=en&view=itissues';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.08 ms |
| checking permissions | 0.02 ms |
| Opening tables | 0.02 ms |
| init | 0.03 ms |
| System lock | 0.02 ms |
| optimizing | 0.02 ms |
| statistics | 0.09 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_latest_issues/tmpl/default.php:52 |
| 11 | require JROOT/modules/mod_latest_issues/tmpl/default.php | JROOT/modules/mod_latest_issues/mod_latest_issues.php:116 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.49 ms After last query: 0.64 ms Query memory: 0.029 MB Memory before query: 38.385 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&id=517&lang=en&view=itissues';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.10 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 0.12 ms |
| end | 0.01 ms |
| query end | 0.02 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_latest_issues/tmpl/default.php:52 |
| 11 | require JROOT/modules/mod_latest_issues/tmpl/default.php | JROOT/modules/mod_latest_issues/mod_latest_issues.php:116 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.16 ms After last query: 0.66 ms Query memory: 0.029 MB Memory before query: 38.399 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_issuetracker&id=513&lang=en&view=itissues';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.03 ms |
| statistics | 0.57 ms |
| preparing | 0.02 ms |
| executing | 0.02 ms |
| Sending data | 0.07 ms |
| end | 0.03 ms |
| query end | 0.02 ms |
| closing tables | 0.04 ms |
| freeing items | 0.08 ms |
| cleaning up | 0.04 ms |
| # | Caller | File and line number |
|---|
| 30 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 29 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 28 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 27 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 26 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 25 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 24 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1548 |
| 23 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 22 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 21 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 20 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 19 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 18 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 17 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 16 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 15 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 14 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 13 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 12 | Joomla\CMS\Router\Route::_() | JROOT/modules/mod_latest_issues/tmpl/default.php:52 |
| 11 | require JROOT/modules/mod_latest_issues/tmpl/default.php | JROOT/modules/mod_latest_issues/mod_latest_issues.php:116 |
| 10 | include JROOT/modules/mod_latest_issues/mod_latest_issues.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 6.64 ms After last query: 1.66 ms Query memory: 0.022 MB Memory before query: 38.433 MB Rows returned: 1
SELECT count(*)
from l6r3h_rquote
WHERE published='1'
AND catid IN ('24','25','26','28','29','30','31','32','33','34','37','38','39','40','41','42','43','44','45','46','47','48','49','50','51','52','53','54','55','56','57','58','59','62','63','64')
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_rquote | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 3092 | 5.00 | Using where |
| Status | Duration |
|---|
| starting | 0.27 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.27 ms |
| init | 0.04 ms |
| System lock | 0.01 ms |
| optimizing | 0.02 ms |
| statistics | 0.02 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 4.54 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 12 | JDatabaseDriver->loadResult() | JROOT/modules/mod_rquotes/helper.php:191 |
| 11 | getDailyRquote() | JROOT/modules/mod_rquotes/mod_rquotes.php:42 |
| 10 | include JROOT/modules/mod_rquotes/mod_rquotes.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 2.03 ms After last query: 0.06 ms Query memory: 0.022 MB Memory before query: 38.439 MB Rows returned: 1
SELECT *
FROM l6r3h_rquote_meta
WHERE id='1'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_rquote_meta | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.34 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.02 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1773 |
| 12 | JDatabaseDriver->loadRow() | JROOT/modules/mod_rquotes/helper.php:195 |
| 11 | getDailyRquote() | JROOT/modules/mod_rquotes/mod_rquotes.php:42 |
| 10 | include JROOT/modules/mod_rquotes/mod_rquotes.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 6.99 ms After last query: 0.06 ms Query memory: 0.022 MB Memory before query: 38.446 MB Rows returned: 3
SELECT *
FROM l6r3h_rquote
WHERE published='1'
AND catid IN ('24','25','26','28','29','30','31','32','33','34','37','38','39','40','41','42','43','44','45','46','47','48','49','50','51','52','53','54','55','56','57','58','59','62','63','64')
AND daily_number = '166'
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_rquote | NULL | ALL | NULL | NO INDEX KEY COULD BE USED | NULL | NULL | 3092 | 0.50 | Using where |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.13 ms |
| init | 0.03 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.01 ms |
| preparing | 0.01 ms |
| executing | 0.00 ms |
| Sending data | 5.74 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.02 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 13 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1701 |
| 12 | JDatabaseDriver->loadObjectList() | JROOT/modules/mod_rquotes/helper.php:222 |
| 11 | getDailyRquote() | JROOT/modules/mod_rquotes/mod_rquotes.php:42 |
| 10 | include JROOT/modules/mod_rquotes/mod_rquotes.php | JROOT/libraries/src/Helper/ModuleHelper.php:200 |
| 9 | Joomla\CMS\Helper\ModuleHelper::renderModule() | JROOT/libraries/src/Document/Renderer/Html/ModuleRenderer.php:98 |
| 8 | Joomla\CMS\Document\Renderer\Html\ModuleRenderer->render() | JROOT/libraries/src/Document/Renderer/Html/ModulesRenderer.php:47 |
| 7 | Joomla\CMS\Document\Renderer\Html\ModulesRenderer->render() | JROOT/libraries/src/Document/HtmlDocument.php:511 |
| 6 | Joomla\CMS\Document\HtmlDocument->getBuffer() | JROOT/libraries/src/Document/HtmlDocument.php:803 |
| 5 | Joomla\CMS\Document\HtmlDocument->_renderTemplate() | JROOT/libraries/src/Document/HtmlDocument.php:577 |
| 4 | Joomla\CMS\Document\HtmlDocument->render() | JROOT/libraries/src/Application/CMSApplication.php:1112 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 3.16 ms After last query: 44.04 ms Query memory: 0.027 MB Memory before query: 38.967 MB Rows returned: 0
SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
WHERE `newurl`='index.php?option=com_osmap&id=1&lang=en&view=html';
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_sh404sef_urls | NULL | ref | newurl | newurl | 573 | const | 1 | 100.00 | Using where |
| Status | Duration |
|---|
| starting | 0.70 ms |
| checking permissions | 0.03 ms |
| Opening tables | 0.49 ms |
| init | 0.15 ms |
| System lock | 0.02 ms |
| optimizing | 0.02 ms |
| statistics | 0.49 ms |
| preparing | 0.03 ms |
| executing | 0.01 ms |
| Sending data | 0.05 ms |
| end | 0.01 ms |
| query end | 0.02 ms |
| closing tables | 0.02 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 26 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1662 |
| 25 | JDatabaseDriver->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:628 |
| 24 | ShlDbClass->loadObject() | JROOT/plugins/system/shlib/shl_packages/db/classes/class.php:442 |
| 23 | ShlDbClass->shlLoadObject() | JROOT/plugins/system/shlib/shl_packages/db/helpers/helper.php:655 |
| 22 | ShlDbHelper::selectObject() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:789 |
| 21 | getSefUrlFromDatabase() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:826 |
| 20 | shGetSefURLFromCacheOrDB() | JROOT/administrator/components/com_sh404sef/sh404sef.class.php:1496 |
| 19 | shSefRelToAbs() | JROOT/administrator/components/com_sh404sef/classes/router.php:1230 |
| 18 | Sh404sefClassRouterInternal->_buildSefRouteInternal() | JROOT/administrator/components/com_sh404sef/classes/router.php:2675 |
| 17 | Sh404sefClassRouter->_buildSefRoute() | JROOT/administrator/components/com_sh404sef/classes/router.php:1084 |
| 16 | Sh404sefClassRouterInternal->buildRule() | Same as call in the line below. |
| 15 | call_user_func_array() | JROOT/libraries/src/Router/Router.php:638 |
| 14 | Joomla\CMS\Router\Router->processBuildRules() | JROOT/libraries/src/Router/SiteRouter.php:661 |
| 13 | Joomla\CMS\Router\SiteRouter->processBuildRules() | JROOT/libraries/src/Router/Router.php:614 |
| 12 | Joomla\CMS\Router\Router->_processBuildRules() | JROOT/libraries/src/Router/Router.php:270 |
| 11 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 10 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 9 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 8 | Joomla\CMS\Router\Route::_() | JROOT/plugins/system/sef/sef.php:110 |
| 7 | PlgSystemSef->onAfterRender() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1118 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.26 ms After last query: 0.82 ms Query memory: 0.023 MB Memory before query: 39.099 MB Rows returned: 1
SELECT alias
FROM l6r3h_kbase_articles
WHERE id = 18
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_kbase_articles | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.06 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.09 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.06 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.05 ms |
| cleaning up | 0.05 ms |
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/components/com_kbase/router.php:81 |
| 14 | KbaseRouter->build() | JROOT/libraries/src/Router/SiteRouter.php:532 |
| 13 | Joomla\CMS\Router\SiteRouter->buildSefRoute() | JROOT/libraries/src/Router/SiteRouter.php:502 |
| 12 | Joomla\CMS\Router\SiteRouter->_buildSefRoute() | JROOT/libraries/src/Router/Router.php:281 |
| 11 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 10 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 9 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 8 | Joomla\CMS\Router\Route::_() | JROOT/plugins/system/sef/sef.php:110 |
| 7 | PlgSystemSef->onAfterRender() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1118 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.15 ms After last query: 0.45 ms Query memory: 0.023 MB Memory before query: 39.107 MB Rows returned: 1
SELECT alias
FROM l6r3h_kbase_articles
WHERE id = 17
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_kbase_articles | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.02 ms |
| executing | 0.01 ms |
| Sending data | 0.02 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/components/com_kbase/router.php:81 |
| 14 | KbaseRouter->build() | JROOT/libraries/src/Router/SiteRouter.php:532 |
| 13 | Joomla\CMS\Router\SiteRouter->buildSefRoute() | JROOT/libraries/src/Router/SiteRouter.php:502 |
| 12 | Joomla\CMS\Router\SiteRouter->_buildSefRoute() | JROOT/libraries/src/Router/Router.php:281 |
| 11 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 10 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 9 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 8 | Joomla\CMS\Router\Route::_() | JROOT/plugins/system/sef/sef.php:110 |
| 7 | PlgSystemSef->onAfterRender() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1118 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.12 ms After last query: 0.42 ms Query memory: 0.023 MB Memory before query: 39.115 MB Rows returned: 1
SELECT alias
FROM l6r3h_kbase_articles
WHERE id = 14
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_kbase_articles | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.04 ms |
| cleaning up | 0.03 ms |
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/components/com_kbase/router.php:81 |
| 14 | KbaseRouter->build() | JROOT/libraries/src/Router/SiteRouter.php:532 |
| 13 | Joomla\CMS\Router\SiteRouter->buildSefRoute() | JROOT/libraries/src/Router/SiteRouter.php:502 |
| 12 | Joomla\CMS\Router\SiteRouter->_buildSefRoute() | JROOT/libraries/src/Router/Router.php:281 |
| 11 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 10 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 9 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 8 | Joomla\CMS\Router\Route::_() | JROOT/plugins/system/sef/sef.php:110 |
| 7 | PlgSystemSef->onAfterRender() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1118 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.09 ms After last query: 0.41 ms Query memory: 0.023 MB Memory before query: 39.123 MB Rows returned: 1
SELECT alias
FROM l6r3h_kbase_articles
WHERE id = 11
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_kbase_articles | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.03 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/components/com_kbase/router.php:81 |
| 14 | KbaseRouter->build() | JROOT/libraries/src/Router/SiteRouter.php:532 |
| 13 | Joomla\CMS\Router\SiteRouter->buildSefRoute() | JROOT/libraries/src/Router/SiteRouter.php:502 |
| 12 | Joomla\CMS\Router\SiteRouter->_buildSefRoute() | JROOT/libraries/src/Router/Router.php:281 |
| 11 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 10 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 9 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 8 | Joomla\CMS\Router\Route::_() | JROOT/plugins/system/sef/sef.php:110 |
| 7 | PlgSystemSef->onAfterRender() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1118 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.08 ms After last query: 0.40 ms Query memory: 0.023 MB Memory before query: 39.132 MB Rows returned: 1
SELECT alias
FROM l6r3h_kbase_articles
WHERE id = 23
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_kbase_articles | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.01 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.03 ms |
| statistics | 0.03 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.26 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/components/com_kbase/router.php:81 |
| 14 | KbaseRouter->build() | JROOT/libraries/src/Router/SiteRouter.php:532 |
| 13 | Joomla\CMS\Router\SiteRouter->buildSefRoute() | JROOT/libraries/src/Router/SiteRouter.php:502 |
| 12 | Joomla\CMS\Router\SiteRouter->_buildSefRoute() | JROOT/libraries/src/Router/Router.php:281 |
| 11 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 10 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 9 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 8 | Joomla\CMS\Router\Route::_() | JROOT/plugins/system/sef/sef.php:110 |
| 7 | PlgSystemSef->onAfterRender() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1118 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.08 ms After last query: 0.39 ms Query memory: 0.023 MB Memory before query: 39.140 MB Rows returned: 1
SELECT alias
FROM l6r3h_kbase_articles
WHERE id = 16
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_kbase_articles | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.03 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/components/com_kbase/router.php:81 |
| 14 | KbaseRouter->build() | JROOT/libraries/src/Router/SiteRouter.php:532 |
| 13 | Joomla\CMS\Router\SiteRouter->buildSefRoute() | JROOT/libraries/src/Router/SiteRouter.php:502 |
| 12 | Joomla\CMS\Router\SiteRouter->_buildSefRoute() | JROOT/libraries/src/Router/Router.php:281 |
| 11 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 10 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 9 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 8 | Joomla\CMS\Router\Route::_() | JROOT/plugins/system/sef/sef.php:110 |
| 7 | PlgSystemSef->onAfterRender() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1118 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.09 ms After last query: 0.40 ms Query memory: 0.023 MB Memory before query: 39.148 MB Rows returned: 1
SELECT alias
FROM l6r3h_kbase_articles
WHERE id = 28
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_kbase_articles | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.04 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.03 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.03 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.01 ms |
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/components/com_kbase/router.php:81 |
| 14 | KbaseRouter->build() | JROOT/libraries/src/Router/SiteRouter.php:532 |
| 13 | Joomla\CMS\Router\SiteRouter->buildSefRoute() | JROOT/libraries/src/Router/SiteRouter.php:502 |
| 12 | Joomla\CMS\Router\SiteRouter->_buildSefRoute() | JROOT/libraries/src/Router/Router.php:281 |
| 11 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 10 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 9 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 8 | Joomla\CMS\Router\Route::_() | JROOT/plugins/system/sef/sef.php:110 |
| 7 | PlgSystemSef->onAfterRender() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1118 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
Query Time: 1.09 ms After last query: 0.40 ms Query memory: 0.023 MB Memory before query: 39.156 MB Rows returned: 1
SELECT alias
FROM l6r3h_kbase_articles
WHERE id = 26
| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
|---|
| 1 | SIMPLE | l6r3h_kbase_articles | NULL | const | PRIMARY | PRIMARY | 4 | const | 1 | 100.00 | NULL |
| Status | Duration |
|---|
| starting | 0.05 ms |
| checking permissions | 0.01 ms |
| Opening tables | 0.02 ms |
| init | 0.02 ms |
| System lock | 0.01 ms |
| optimizing | 0.01 ms |
| statistics | 0.04 ms |
| preparing | 0.01 ms |
| executing | 0.01 ms |
| Sending data | 0.01 ms |
| end | 0.01 ms |
| query end | 0.01 ms |
| closing tables | 0.01 ms |
| freeing items | 0.03 ms |
| cleaning up | 0.02 ms |
| # | Caller | File and line number |
|---|
| 16 | JDatabaseDriverMysqli->execute() | JROOT/libraries/joomla/database/driver.php:1740 |
| 15 | JDatabaseDriver->loadResult() | JROOT/components/com_kbase/router.php:81 |
| 14 | KbaseRouter->build() | JROOT/libraries/src/Router/SiteRouter.php:532 |
| 13 | Joomla\CMS\Router\SiteRouter->buildSefRoute() | JROOT/libraries/src/Router/SiteRouter.php:502 |
| 12 | Joomla\CMS\Router\SiteRouter->_buildSefRoute() | JROOT/libraries/src/Router/Router.php:281 |
| 11 | Joomla\CMS\Router\Router->build() | JROOT/libraries/src/Router/SiteRouter.php:155 |
| 10 | Joomla\CMS\Router\SiteRouter->build() | JROOT/libraries/src/Router/Route.php:144 |
| 9 | Joomla\CMS\Router\Route::link() | JROOT/libraries/src/Router/Route.php:93 |
| 8 | Joomla\CMS\Router\Route::_() | JROOT/plugins/system/sef/sef.php:110 |
| 7 | PlgSystemSef->onAfterRender() | JROOT/libraries/joomla/event/event.php:70 |
| 6 | JEvent->update() | JROOT/libraries/joomla/event/dispatcher.php:160 |
| 5 | JEventDispatcher->trigger() | JROOT/libraries/src/Application/BaseApplication.php:108 |
| 4 | Joomla\CMS\Application\BaseApplication->triggerEvent() | JROOT/libraries/src/Application/CMSApplication.php:1118 |
| 3 | Joomla\CMS\Application\CMSApplication->render() | JROOT/libraries/src/Application/SiteApplication.php:778 |
| 2 | Joomla\CMS\Application\SiteApplication->render() | JROOT/libraries/src/Application/CMSApplication.php:231 |
| 1 | Joomla\CMS\Application\CMSApplication->execute() | JROOT/index.php:49 |
15 × SELECT `oldurl`, `dateadd`
FROM l6r3h_sh404sef_urls
8 × SELECT `template`
FROM `l6r3h_template_styles`
8 × SELECT alias
FROM l6r3h_kbase_articles
6 × SELECT `id`
FROM `l6r3h_menu`
3 × SELECT a.`id`, a.`title`, a.`alias`
FROM `l6r3h_easyblog_tag` AS a
LEFT JOIN `l6r3h_easyblog_post_tag` AS b
ON a.`id`= b.`tag_id`
2 × SELECT `extension_id` AS `id`,`element` AS `option`,`params`,`enabled`
FROM `l6r3h_extensions`
2 × SELECT *
FROM l6r3h_languages
2 × SELECT *
FROM `l6r3h_easyblog_acl_group`
1 × SELECT `data`
FROM `l6r3h_session`
1 × SELECT `session_id`
FROM `l6r3h_session`
1 × SELECT id, rules
FROM `l6r3h_viewlevels
1 × SELECT b.id
FROM l6r3h_usergroups AS a
LEFT JOIN l6r3h_usergroups AS b
ON b.lft <= a.lft
AND b.rgt >= a.rgt
1 × SELECT `folder` AS `type`,`element` AS `name`,`params` AS `params`,`extension_id` AS `id`
FROM l6r3h_extensions
1 × SELECT m.id, m.menutype, m.title, m.alias, m.note, m.path AS route, m.link, m.type, m.level, m.language,`m`.`browserNav`, m.access, m.params, m.home, m.img, m.template_style_id, m.component_id, m.parent_id,e.element as component
FROM l6r3h_menu AS m
LEFT JOIN l6r3h_extensions AS e
ON m.component_id = e.extension_id
1 × SELECT `params`
FROM l6r3h_extensions
1 × SELECT *
FROM l6r3h_komento_configs
1 × SELECT *
FROM `l6r3h_sh404sef_aliases`
1 × SELECT *
FROM l6r3h_sh404sef_aliases
1 × SELECT *
FROM l6r3h_sh404sef_pageids
1 × SELECT `oldurl`, `newurl`, `dateadd`, `id`, `cpt`, `rank`
FROM l6r3h_sh404sef_urls
1 × SELECT COUNT(*)
FROM l6r3h_rantispam_banip
1 × SELECT `id`,`name`,`rules`,`parent_id`
FROM `l6r3h_assets`
1 × SELECT *
FROM l6r3h_acysms_confi
1 × SELECT id, home, template, s.params
FROM l6r3h_template_styles as s
LEFT JOIN l6r3h_extensions as e
ON e.element=s.template
AND e.type='template'
AND e.client_id=s.client_id
1 × SELECT *
FROM l6r3h_easyblog_configs
1 × SELECT *
FROM `l6r3h_easyblog_post`
1 × SELECT id, created_by
FROM`l6r3h_easyblog_post`
1 × SELECT *
FROM `l6r3h_easyblog_uploader_tmp`
1 × SELECT a.`id`
FROM `l6r3h_easyblog_post` as a
inner join `l6r3h_easyblog_revisions` as b
on a.`id` = b.`post_id`
1 × SELECT *
FROM `l6r3h_menu`
1 × SELECT `oldurl`
FROM l6r3h_sh404sef_urls
1 × SELECT *
FROM `l6r3h_easyblog_acl`
1 × SELECT *
FROM l6r3h_easyblog_category
1 × SELECT COUNT(1)
FROM `l6r3h_easyblog_category_acl` as a
LEFT JOIN `l6r3h_easyblog_category` as b
ON a.`category_id` = b.`id`
1 × select a.`id`, a.`title`, a.`alias`, a.`private`, a.`parent_id`, a.`avatar`, a.`description`
from `l6r3h_easyblog_category` as a
1 × SELECT COUNT(1) AS `cnt`
FROM `l6r3h_easyblog_post_category` AS `a`
INNER JOIN `l6r3h_easyblog_post` AS `b`
ON a.`post_id` = b.`id`
AND b.`published`='1'
INNER JOIN `l6r3h_easyblog_category` AS `c`
ON a.`category_id` = c.`id`
INNER JOIN `l6r3h_users` AS `uu`
ON b.`created_by` = uu.`id`
AND b.`access` = '0'
1 × SELECT COUNT(1)
FROM `l6r3h_easyblog_post` AS a
LEFT JOIN `l6r3h_easyblog_featured` as f
ON a.`id` = f.`content_id`
AND f.`type` = 'post'
INNER JOIN `l6r3h_users` AS uu
ON a.`created_by` = uu.`id`
and uu.`block` = 0
1 × SELECT a.*, ifnull(f.`id`, 0) as `featured`
FROM `l6r3h_easyblog_post` AS a
LEFT JOIN `l6r3h_easyblog_featured` as f
ON a.`id` = f.`content_id`
AND f.`type` = 'post'
INNER JOIN `l6r3h_users` AS uu
ON a.`created_by` = uu.`id`
and uu.`block` = 0
1 × SELECT COUNT(1)
FROM `l6r3h_easyblog_category_acl`
1 × SELECT COUNT(1) as `voted`, `uid`
FROM `l6r3h_easyblog_ratings`
1 × SELECT AVG(`value`) AS `ratings` ,COUNT(1) AS `total` ,`uid`
FROM `l6r3h_easyblog_ratings` AS a
1 × SELECT a.`post_id`, COUNT(1) AS `count`
FROM `l6r3h_easyblog_comment` AS a
LEFT JOIN `l6r3h_users` AS uu
ON a.`created_by` = uu.`id`
1 × select a.*, b.`post_id`, b.`primary`
from `l6r3h_easyblog_category` as a
inner join `l6r3h_easyblog_post_category` as b
on a.`id` = b.`category_id`
1 × select a.*, b.`post_id`
from `l6r3h_easyblog_tag` as a
inner join `l6r3h_easyblog_post_tag` as b
on a.`id` = b.`tag_id`
1 × select a.*
from `l6r3h_easyblog_revisions` as a
1 × select u.*, e.`id` as `eb_id`, e.`nickname`, e.`avatar`, e.`description`, e.`url`, e.`params` as `eb_params`, e.`published` as `eb_published`, e.`title` as `eb_title`, e.`biography`, e.`permalink`, e.`custom_css`, e.`ordering`
from `l6r3h_users` as u
left join `l6r3h_easyblog_users` as e
ON u.`id` = e.`id`
1 × SELECT *
FROM `l6r3h_users`
1 × SELECT `g`.`id`,`g`.`title`
FROM `l6r3h_usergroups` AS g
INNER JOIN `l6r3h_user_usergroup_map` AS m
ON m.group_id = g.id
1 × select `a`.`id` as `cat_fg_id`, `a`.`category_id` as `cat_fg_category_id`, `a`.`group_id` as `cat_fg_group_id`, `fg`.`id` as `fg_id`, `fg`.`title` as `fg_title`, `fg`.`description` as `fg_description`, `fg`.`created` as `fg_created`, `fg`.`state` as `fg_state`, `fg`.`read` as `fg_read`, `fg`.`write` as `fg_write`, `fg`.`params` as `fg_params`, `f`.`id` as `f_id`, `f`.`group_id` as `f_group_id`, `f`.`title` as `f_title`, `f`.`help` as `f_help`, `f`.`state` as `f_state`, `f`.`required` as `f_required`, `f`.`type` as `f_type`, `f`.`params` as `f_params`, `f`.`created` as `f_created`, `f`.`options` as `f_options`, `f`.`ordering` as `f_ordering`,`fv`.`id` as `fv_id`, `fv`.`field_id` as `fv_field_id`, `fv`.`post_id` as `fv_post_id`, `fv`.`value` as `fv_value`
from `l6r3h_easyblog_category_fields_groups` as a
inner join `l6r3h_easyblog_post_category` as p
on `a`.`category_id` = `p`.`category_id`
inner join `l6r3h_easyblog_fields_groups` as fg
on `a`.`group_id` = `fg`.`id`
inner join `l6r3h_easyblog_fields` as f
on `fg`.`id` = `f`.`group_id`
left join `l6r3h_easyblog_fields_values` as fv
on `fv`.`field_id` = `f`.`id`
and `fv`.`post_id` = `p`.`post_id`
LEFT JOIN `l6r3h_easyblog_fields_groups_acl` AS acl
ON fg.`id` = acl.`group_id`
1 × select *
from `l6r3h_easyblog_meta`
1 × SELECT `id`
FROM `l6r3h_easyblog_subscriptions`
1 × SELECT *
FROM l6r3h_easyblog_meta
1 × SELECT m.id, m.title, m.module, m.position, m.content, m.showtitle, m.params, mm.menuid
FROM l6r3h_modules AS m
LEFT JOIN l6r3h_modules_menu AS mm
ON mm.moduleid = m.id
LEFT JOIN l6r3h_extensions AS e
ON e.element = m.module
AND e.client_id = m.client_id
1 × SELECT `group_id`
FROM `l6r3h_user_usergroup_map`
1 × SELECT DISTINCT a.id, a.title, a.name, a.checked_out, a.checked_out_time, a.note, a.state, a.access, a.created_time, a.created_user_id, a.ordering, a.language, a.fieldparams, a.params, a.type, a.default_value, a.context, a.group_id, a.label, a.description, a.required,l.title AS language_title, l.image AS language_image,uc.name AS editor,ag.title AS access_level,ua.name AS author_name,g.title AS group_title, g.access as group_access, g.state AS group_state, g.note as group_note
FROM l6r3h_fields AS a
LEFT JOIN `l6r3h_languages` AS l
ON l.lang_code = a.language
LEFT JOIN l6r3h_users AS uc
ON uc.id=a.checked_out
LEFT JOIN l6r3h_viewlevels AS ag
ON ag.id = a.access
LEFT JOIN l6r3h_users AS ua
ON ua.id = a.created_user_id
LEFT JOIN l6r3h_fields_groups AS g
ON g.id = a.group_id
LEFT JOIN `l6r3h_fields_categories` AS fc
ON fc.field_id = a.id
1 × SELECT *
FROM l6r3h_sh404sef_metas
1 × SELECT `pageid`
FROM l6r3h_sh404sef_pageids
1 × SELECT *
FROM `l6r3h_kunena_configuration`
1 × SELECT *
FROM l6r3h_acymailing_confi
1 × SELECT *
FROM l6r3h_acymailing_list
1 × SELECT identifier
from `l6r3h_ipmap_robots`
1 × SELECT *
FROM `l6r3h_ipmap_location`
1 × SELECT @n := IFNULL(MAX(ordering),1)
from `l6r3h_ipmap_location
1 × SELECT *
FROM l6r3h_ipmap_location
1 × SELECT version
from `l6r3h_it_meta`
1 × SELECT i.id, i.actual_resolution_date, i.alias, i.issue_summary, p.title ,p.id AS project_id ,s.status_name AS status
FROM l6r3h_it_issues as i
LEFT JOIN l6r3h_it_projects as p
on i.related_project_id = p.id
LEFT JOIN l6r3h_it_status as s
on i.status = s.id
1 × SELECT a.title AS text, a.id AS value, a.parent_id as parentid
FROM l6r3h_it_projects AS
1 × SELECT id
FROM `l6r3h_it_projects`
1 × SELECT count(*)
from l6r3h_rquote
1 × SELECT *
FROM l6r3h_rquote_meta
1 × SELECT *
FROM l6r3h_rquote

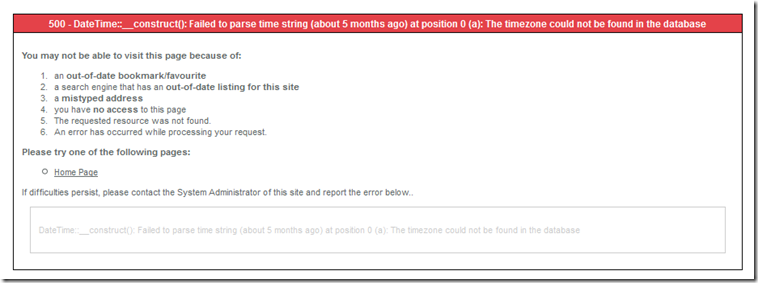


 Since we started mapping IP addresses of persistent attempts to submit SPAM on our live site, it is obvious that Miami in the US is one of the most persistemt source. Already even though it is only the fourth day of the month we can see 128 attempts to submit SPAM messages.
Since we started mapping IP addresses of persistent attempts to submit SPAM on our live site, it is obvious that Miami in the US is one of the most persistemt source. Already even though it is only the fourth day of the month we can see 128 attempts to submit SPAM messages.